Best Intruder Alternatives and Competitors
Discover the best Intruder alternatives and top competitors for 2025. Compare leading vulnerability scanning tools for web application security and threat detection.

Bhagyashree
Jul 23, 2025
Intruder is one of the top cloud based vulnerability scanner, however it may not be suitable for all security teams. So, in such cases, it is viable to consider other platforms that offer unique advantages in asset discovery, accuracy and process integration. These alternative platforms are tailored to wide spectrum of security needs such as coverage of full stack vulnerability, open-source freedom, CI/CD integration and more.
Exploring other alternatives to Intruder. This blog explores the Top 10 Intruder alternatives and the unique features each alternative offers.
Akto
Akto is among the best modern AI-powered API security platform that encourages DevSecOps and AppSec teams to secure API’s from code-to-runtime. It is designed for instant deployment and can be setup in minutes and scales to manage hundreds of thousands of APIs.

Image source: Akto
Features:
Runs more than 1000 tests which includes OWASP API top 10 threats, flaws in authorization and authentication, and business logic vulnerabilities.
Catalogs all types of APIs through code and traffic connectors such as Burp, GitHub etc.
Easily integrates with CI/CD and other DevSecOps pipelines to test APIs.
AI-powered runtime protection and continuous sensitive data monitoring and ability to define custom data types
Monitors various types of misconfigurations continuously with risk scoring and actual exploit potential
Ideal For:
DevSecOps, engineering teams and enterprises that are looking to integrate security into their CI/CD pipelines such as shift-left practices looking to automate API testing before deployment.
Invicti
Invicti Security is one of the top AppSec platform designed for DAST (Dynamic Application Security Testing). The platform specializes in automated discovery, verification, and mitigation of vulnerabilities in web apps, APIs, containers, and more with zero noise and proof based scanning accuracy.

Image source: Invicti
Features:
Discover & crawl all web assets and APIs that includes undocumented ones and combined DAST/IAST instrumentation
Proof-based scanning™ confirms real issues and lowers false positives.
DAST + IAST hybrid scanning for broader and accurate detection which covers signature and behavioral flaws
Predictive risk scoring to ensure efficient testing and focused remediation
CI/CD & workflow integration and issue trackers that automates scan scheduling, gives detailed developer remediation guidance, and enables centralized RBAC management.
Ideal For:
DevSecOps teams seeking a platform that comprises DAST, IAST, SAST, SCA, API and container that scans all centrally managed and automated.
Burp Suite
Burp Suite is a one of the popular web application security platform. It specializes in manual and automated penetration testing by offering suite of trusted tools like proxy, scanner, intruder, repeater, collaborator, sequencer, and more

Image source: Burp Suite
Features:
Burp AI for vulnerability investigation, message understanding, false positive filtering and automated recorded logins
Industry-leading dynamic scanner crawls complex apps and APIs finds classic and zero‑day vulnerabilities, with active and passive scans
Powerful tools for customized fuzzing, request tampering, session token analysis, out‑of‑band (OAST) testing, plus utilities like decoder, comparer, logger, DOM Invader and more
Extensibility & CI/CD Integration for multi‑user roles and rich reporting for continuous AppSec workflows.
Capture, inspect, and manipulate HTTP/S and WebSocket traffic in real time.
Ideal For:
DevSecOps & CI/CD environments, modern web & API Applications who are looking to integrate security testing into pipelines, gating releases with dynamic scans and false‑positive reduction.
Tenable Nessus
Tenable is a well known global exposure management platform that focuses on exposing and mitigating priority security gaps that threaten enterprises’ attack surfaces from IT infrastructure and cloud environments to OT, IoT, identity, and applications. It is with a unified platform that merges visibility, contextual risk analytics, and automation across complete cyber exposure ecosystem
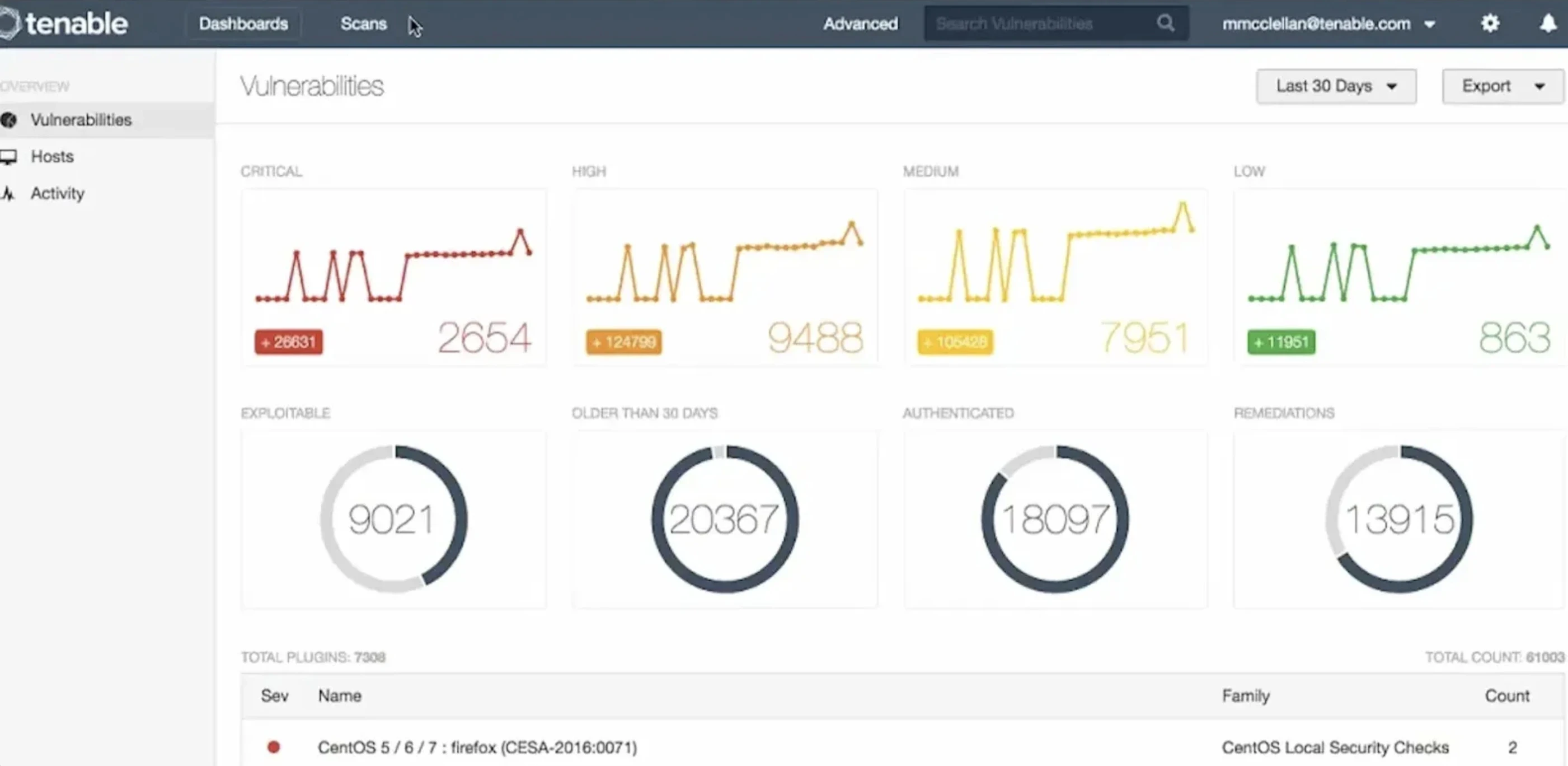
Image source: Tenable
Features:
Unified exposure management platform via (Tenable One) that offers comprehensive inventory, attack-path mapping, predictive prioritization, and actionable insights
World-class vulnerability management through built-in threat insights and dynamic scoring (CVSS, EPSS, VPR)
Cloud-native application protection (CNAPP) and DevSecOps integrations for IaC, container, and Kubernetes environments
OT/IoT & asset exposure visibility by mapping IT-OT interactions and spotting vulnerabilities in SCADA/ICS devices
Identity-aware exposure controls like CIEM and Just-in-time access to implement least privilege
Ideal For:
DevSecOps, Cloud-first organizations and Enterprises with complex attack surfaces, looking to utilize CNAPP and IaC integrations with cloud-native visibility and security.
Wiz
Wiz is one of the renowned agentless cloud-native security platform that specializes in offering unified protection across various environments. It quickly scans infrastructure without any installation overhead and identifies vulnerabilities, misconfigurations, IAM risks, secrets, data exposure, and active threats that enriched by a cloud risk graph engine.
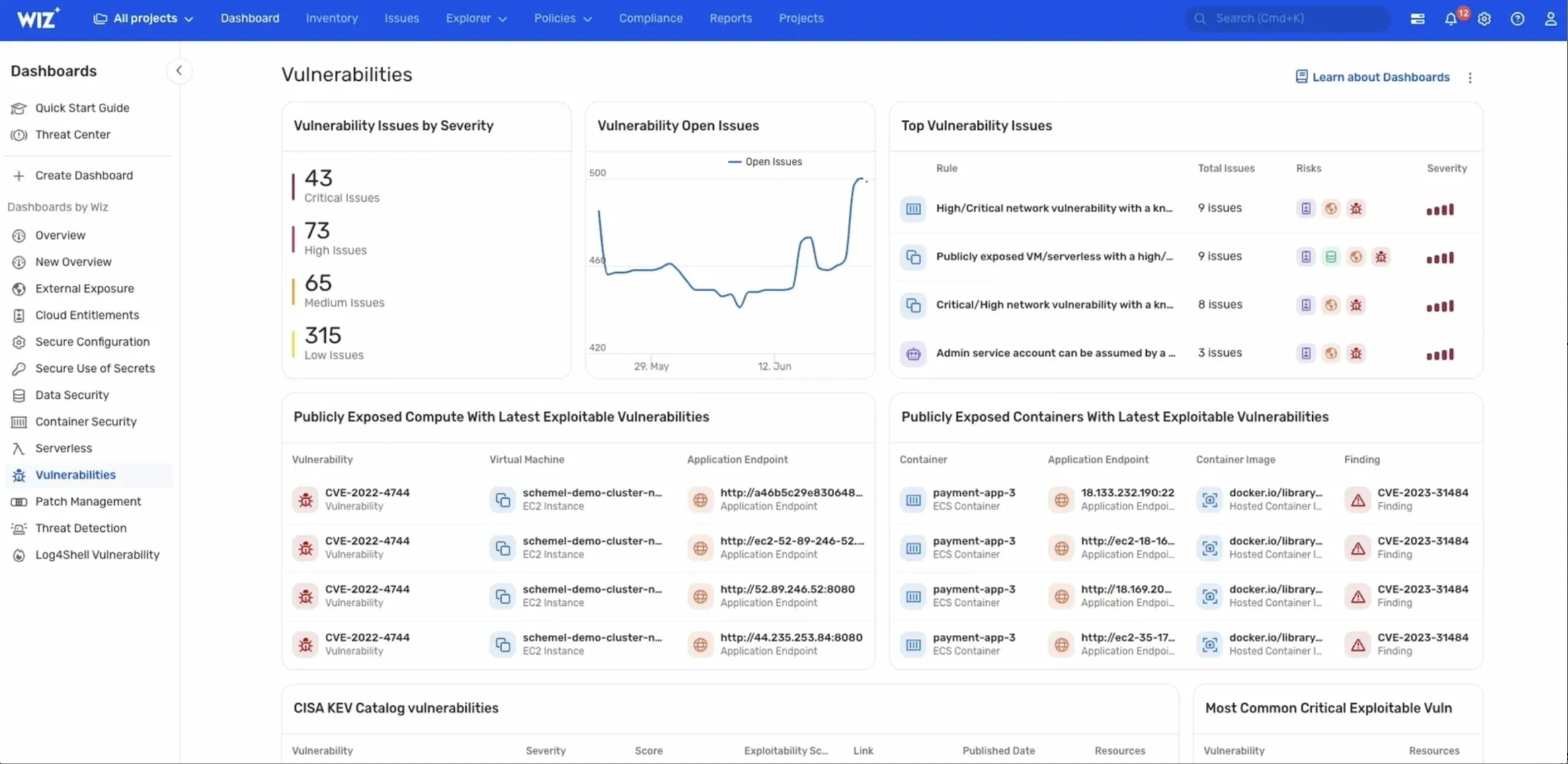
Image source: Wiz
Features:
Comprehensive CNAPP Platform that combines CSPM, CWPP, CDR, CIEM, IaC scanning, container security, and data security posture management (DSPM) into one platform.
Continuous scanning of container images and runtime workloads for vulnerabilities and active threats with registry and kubernetes cluster coverage
Provides out-of-the-box detection rules, cloud-native anomaly identification and seamless integrations with SIEM/SOAR/XDR platforms to detect and respond to threats quickly
Shift‑left security from code to cloud and prioritized fix guidance
Cloud risk graph & toxic pairs detection from misconfiguration to data breach
Ideal For:
Cloud-first enterprises, SecOps, DevOps and AppSec teams looking for cloud-native threat response, anomaly detection, and automated alerting directly in the cloud context and embrace shift-left, with integrated security in IDEs and CI/CD workflows.
Snyk
Snyk is one of the renowned developer first security platform. It offers complete suite that secures code, dependencies, containers and infrastructure-as-code with AI-powered insights from its strong vulnerability database.
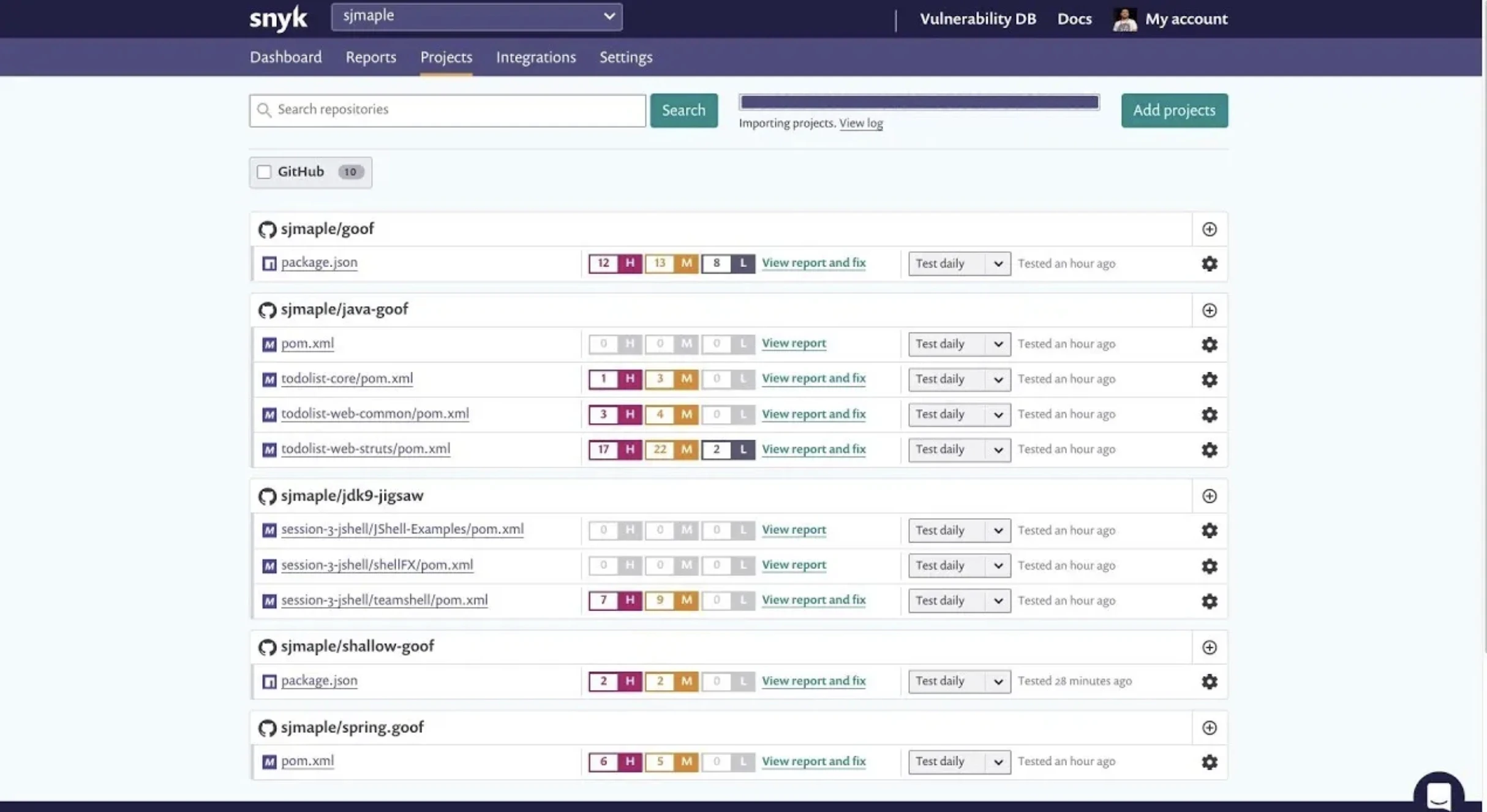
Image source: Snyk
Features:
Protection Across the SDLC such as SAST for source code, dependency scanning, image security, infrastructure-as-code, application risk analytics, and API & Web scanning
Integration into dev IDEs, CLI, Git repos, and CI/CD pipelines by providing security feedback with auto-remediation and policy automation.
AI-Enabled trust platform to provide intelligent prioritization and code-driven security insights that align with developer velocity.
Risk-based issue prioritization & fix guidance for dependencies while reducing noise and focusing on high-impact areas.
Visibility & governance at scale to help security teams manage risk across large codebases.
Ideal For:
Software teams using open-source, enterprises adopting AI and modern SDLC looking for scan-and-fix across all layers, and context-aware vulnerability insights that match development speed.
Detectify
Detectify is a modern AppSec platform that combines dynamic scanning (DAST) with advanced external attack surface management (EASM). It continuously discovers and classifies Internet‑facing assets like domains, subdomains, ports, APIs and automatically launches intelligent, payload-based scans launched from a community of ethical hackers via its crowdsource research program
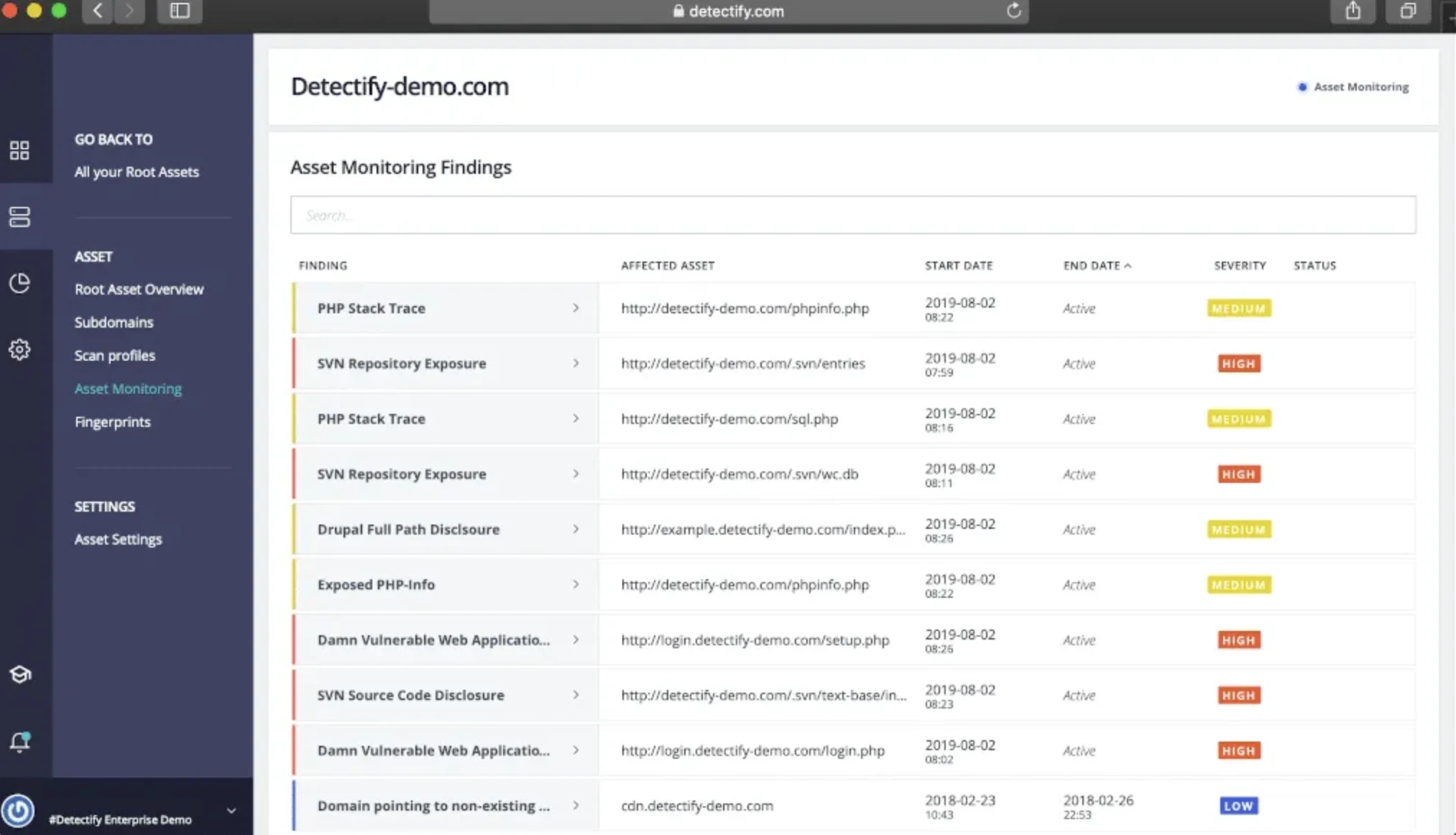
Image source: Detectify
Features
Continuously discovers your public DNS footprint which includes domains, subdomains, ports with no manual setup.
Advanced crawler and engine that intelligently renders complex web apps like authenticated areas for thorough discovery and vulnerability detection.
Utilizes a global community of ethical hackers who submit modules and zero‑days. These are integrated into Detectify's engine which leads to hundreds of modules and continuous 0‑day coverage.
AI‑Led scan recommendations (Alfred AI) automatically classifies assets and highlights critical apps others miss.
Custom policies & integrations enables flexible team structures, dedicated support, and enterprise-grade control.
Ideal For:
Security teams, AppSec teams that are looking for full attack‑surface visibility across domains, APIs, services and ports with minimal overhead.
Beagle Security
Beagle security is a well known SaaS based, AI-powered platform that offers automated penetration testing for web applications, REST APIs and GraphQL endpoints. It simulates human like hacking using AI-driven tests which covers 3,000+ test cases which has OWASP Top 10, zero-day exploits, and business logic vulnerabilities. The platform is designed continuously scan assets and deliver easy-to-understand reports that support various compliance frameworks.
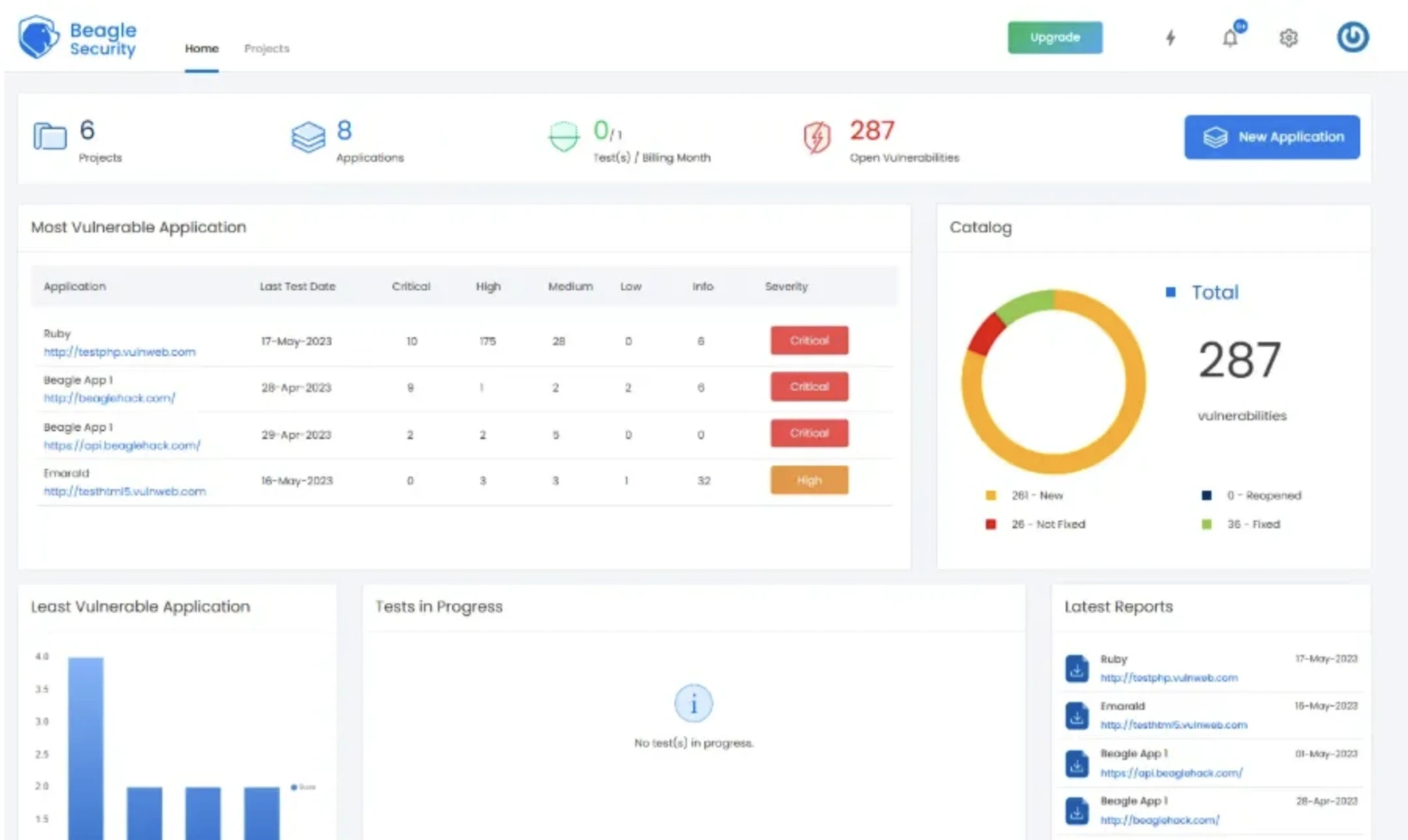
Image source: Beagle security
Features:
AI-powered automated penetration testing to thoroughly probe web apps and APIs such as authenticated flows, with lower false positives
API & GraphQL security testing to detect API-specific vulnerabilities and business logic issues
Continuous asset discovery, scheduled scanning and CI/CD integrations to maintain continuous security coverage.
Generates reports with LLM‑powered recommendations, proof-of-exploit evidence, severity classification, and compliance mapping.
DevSecOps & toolchain integrations like slack, jira, asana, Trello which allows automated alerting, ticket creation, and workflow automation.
Ideal For:
Teams that manage APIs & GraphQL who require dedicated coverage beyond standard web scanning.
Crowdstrike Falcon Spotlight
CrowdStrike falcon spotlight is a leading cybersecurity platform. It aims to unify and improve proactive security across modern hybrid environments. The platform help consolidate external and internal attack surface management, network assessments, misconfiguration detection, attack path analytics, risk-based vulnerability management and automated remediation driven by AI and falcon agent.

Image source: Crowdstrike falcon
Features:
All API interactions are logged and monitored which allows detection of malicious use or compromised credentials .
Automated remediation via API & falcon fusion such as isolating networked devices or auto assigning remediation tickets
APIs expose Spotlight vulnerability data such as recommended remediations and asset associations which allows automated ingestion into ticketing or reporting systems
Integrated API–driven vulnerability ingestion directly allows unified exposure visibility across systems
Users can call API endpoints to retrieve full asset inventories which allows external audit pipelines or custom dashboards .
Ideal For:
DevSecOps looking for recommended mitigation strategies and vulnerability intelligence into DevOps pipelines and ticket systems to close issues at the earliest.
InsightVM
InsightVM is a well known for vulnerability risk management solution. It offers comprehensive and continuous visibility across on-premise, cloud, container, virtual, and remote IT environments, using both agent based and agentless scanning. InsightVM utilizes a unified vulnerability database, live dashboards, and adaptive analytics to help security teams identify threats, prioritize risk, and simplify remediation efforts which enables real-time vulnerability reduction.
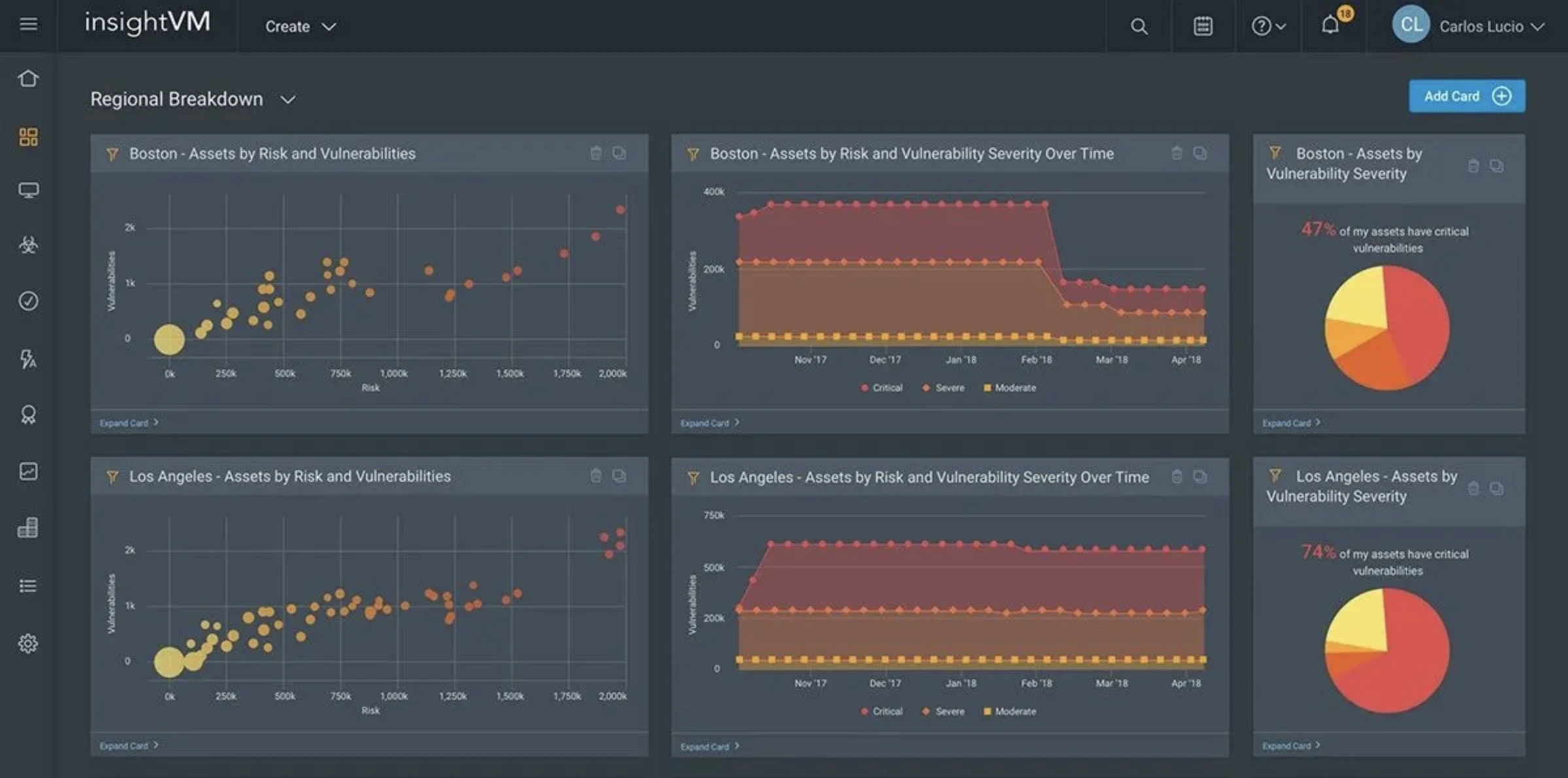
Image source: InsightVM
Features:
Built-in remediation projects enables security teams to assign tasks, integrate with tools, track progress, and validate fixes automatically
Live interactive dashboards & reporting offer indepth real-time insights into exposures and customizable reporting.
Offers RESTful APIs, integrations with SIEM, patching systems, cloud platforms, Metasploit, and more which improves automation and ecosystem leverage
Utilizes AI-driven active risk scoring that incorporates exploitability, business context, attacker behavior and threat intelligence which is beyond traditional CVSS
Comprehensive Asset Discovery & Scanning that ensures no gaps in coverage and even includes cloud misconfiguration checks.
Ideal For:
Security teams, cross-functional teams that managing various environments such as endpoints, cloud, virtual, and containers that requires centralized vulnerability visibility and context aware risk prioritization.
Final Thoughts
Akto is a perfect alternative to intruder and also serves an important role in offering comprehensive API Security. It has a vast library of over 1000 security tests which also includes OWASP top 10 vulnerabilities. The platform provides flexible deployments options such as cloud based, self hosted, or local deployments which allows security teams to choose the ideal setup that fits the business and compliance requirement.
Akto recently introduced industry-first agentic AI suite for API security with groundbreaking AI features for Modern Appsec teams. Book a API security demo today to learn more!
