NIST Releases Version 2.0 : 6 Key Features of NIST CyberSecurity Framework 2.0
Explore the key features and effective implementation of the NIST Cybersecurity Framework 2.0. This comprehensive guide provides insights on managing cybersecurity risks in organizations of all sizes and sectors.

Ankita
Feb 29, 2024
Understanding the NIST Cybersecurity Framework
The NIST Cybersecurity Framework is a comprehensive guide created by the National Institute of Standards and Technology (NIST) to help organizations manage their cybersecurity risks. It provides standards, guidelines, and best practices to manage cybersecurity risks in a cost-effective way. The framework is designed to be applicable to organizations of any size, sector, or maturity level.
What is the NIST Cybersecurity Framework 2.0?
The NIST CSF 2.0 version is a comprehensive cybersecurity framework that is designed to help organizations of all sizes and sectors manage their cybersecurity risks effectively. This framework not only provides guidance for implementing effective cybersecurity practices, but it also emphasizes the importance of continuous improvement and stakeholder feedback.
The CSF 2.0 is structured around six main Functions — Govern, Identify, Protect, Detect, Respond, and Recover. Collectively, these Functions create a holistic approach to managing cybersecurity risk.

In February 2024, NIST completed the first significant revision of the framework since it was first introduced in 2014.
Here are some key features of the CSF 2.0:
Broadened Scope: CSF 2.0 extends its influences beyond just critical infrastructure sectors. It now assists a wider range of organizations, providing guidance to manage cybersecurity risks effectively.
Universal Guidance: The Framework offers high-level cybersecurity outcomes applicable to entities irrespective of their size, sector, or maturity, thereby enhancing their ability to comprehend, evaluate, prioritize, and communicate cybersecurity efforts.

Flexible Approach: CSF 2.0 proposes a taxonomy of cybersecurity outcomes without enforcing specific practices or controls. It directs to resources for achieving these outcomes, making it adaptable for diverse use cases.
Governance Emphasis: The updated Framework highlights the crucial role of governance in managing cybersecurity risks, aligning it with enterprise risk management strategies and stressing the incorporation of cybersecurity into total organizational governance.
Supply Chain Security: The CSF 2.0 stresses the importance of cybersecurity within supply chains, advocating for comprehensive risk management programs that include due diligence and risk assessments for suppliers and third parties.
Adoption of Profiles and Tiers: The Framework encourages creating and using Profiles to customize cybersecurity strategies to specific organizational needs or sector requirements, and utilizing Tiers to help organizations assess their risk management processes and cybersecurity posture.

Before we delve deeper into the the guide of CSF 2.0, Let’s understand with a case study.
Hypothetical Example Case Study
Imagine a Company Acme Inc, an e-commerce platform, adopted the CSF 2.0 to secure their online transactions and customer data. By utilizing the Detect and Respond functions, they were able to quickly identify and mitigate any cyber threats, thereby minimizing the impact on their operations and customer confidence.
Step-by-Step Guide to Implementing CSF 2.0
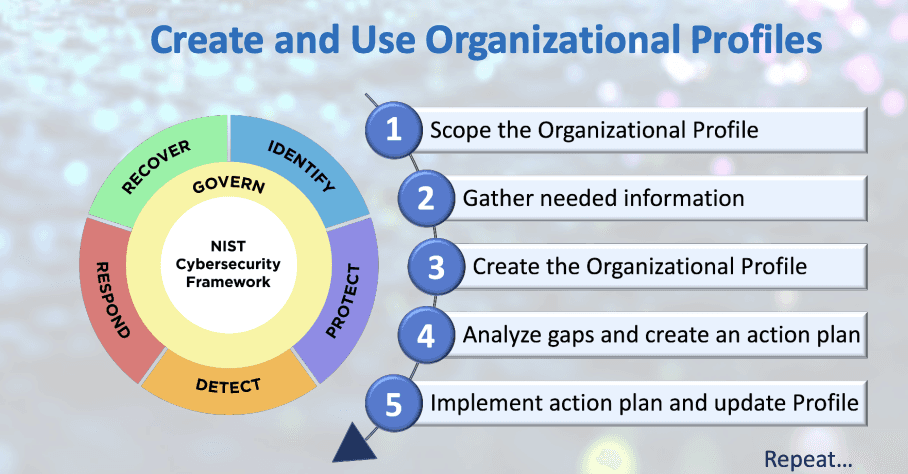
Step 1: Define the Scope of the Organizational Profile
Define the high-level context for the Profiles by setting the scope. You can create multiple Organizational Profiles, each with a different scope. When defining your Profile's scope, consider the following questions:
What purpose does the Organizational Profile serve?
Does the Profile cover the entire organization or specific divisions, data assets, technology assets, products and services, and/or partners and suppliers?
Will the Profile cover all types of cybersecurity threats, vulnerabilities, attacks, and defenses, or only specific types?
Who will develop, review, and operationalize the Profile?
Who will be accountable for setting goals to achieve the target outcomes?
Step 2: Gather Necessary Information
Gather the necessary information, which may include organizational policies, risk management priorities, resources, and cybersecurity standards. The sources you'll need will depend on your use case, the elements your Profiles will capture, and the level of detail you require.
Step 3: Create the Organizational Profile
Determine the supporting information each Profile should include for the selected CSF outcomes. Steps for creating an Organizational Profile are:
Download and customize the latest CSF Organizational Profile template spreadsheet.
Include applicable cybersecurity outcomes for your use case and document reasons as needed.
Document current cybersecurity Practices in the Current Profile columns. Detailed entries can provide better insights for later steps.
Document cybersecurity Goals and plans for achieving them in the Target Profile columns. The entries can be based on CSF Informative References, new cybersecurity requirements, new technologies, and trends in cyber threat intelligence.
Use the Priority field to highlight the importance of each Goal.

Example organization profile
Step 4: Analyze Gaps and Develop an Action Plan
Analyze the differences between the Current and Target Profiles to identify gaps. Then, develop a prioritized action plan to address these gaps. By using Profiles in this manner, your organization can make informed decisions about improving cybersecurity risk management in a prioritized and cost-effective way.
Step 5: Implement the Action Plan and Update the Profile
Implement the Action Plan and update the Profile through a combination of management, programmatic, and technical controls. Use the Organizational Profile to track the implementation status as these controls are implemented. Monitor controls and associated risks through Key Performance Indicators (KPI) and Key Risk Indicators (KRI).
Observe cyber risks beyond Risk Tolerance through Risk Assessments. Consider activities that follow your Action Plan as part of an ongoing cyber risk management program. Leverage Risk Tolerance statements in Risk Assessments when identifying risks, as well as determining the likelihood and impact of those risks. Updates to the Organizational Profile can result from changes in risks, likelihoods, and/or impacts.

Roles and Responsibilities in Implementing CSF 2.0:
Role of the Chief Information Security Officer (CISO):
Strategic Planning: As a CISO, You must understand the core functions of the CSF 2.0: Identify, Protect, Detect, Respond, and Recover, integrating them into the organization's broader security plan.
Risk Management: Use the CSF to identify potential security threats, prioritize them based on severity, and allocate resources to prevent or mitigate these risks.
Compliance and Reporting: You can use the Framework to streamline the compliance process and create more transparent communication channels with stakeholders about the organization's cybersecurity posture.
Role of the Security Manager:
Implementation: The Security Manager is the on-ground executor. You must apply the CSF to secure operations, updating policies, procedures, and controls to align with the Framework.
Team Alignment: Align the team and help them understand their roles in implementing the Framework and maintaining ongoing cybersecurity efforts.
Technology Alignment: Ensure that security investments align with the Framework, enhancing the organization's cybersecurity defenses.
Role of the Security Analyst:
Detailed Assessment: Conduct detailed risk assessments and vulnerability analyses, guided by the CSF, to uncover any potential security threats.
Continuous Monitoring: Use the Framework to develop a robust monitoring strategy that includes detecting, analyzing, and responding to cybersecurity events in real-time.
Incident Response: Use the CSF's guidance to improve plans for responding to cybersecurity incidents and strategies for recovering afterward.
Role of the Security Champion:
Training and Awareness: Develop training programs based on the CSF to enhance cybersecurity awareness and practices among all employees.
Recruitment and Onboarding: Integrate cybersecurity framework understanding into job descriptions and onboarding processes.
Legal and Compliance Officer:
Regulatory Alignment: Map the CSF to existing regulatory requirements to ensure compliance and to streamline reporting.
Contract Management: Ensure that contracts with third parties align with the CSF's guidelines on cybersecurity.
NIST Guidelines to Secure your Microservices Architecture and APIs
In this NIST published document, NIST lays down a foundation for organizations to secure their Microservices Architecture and APIs. Here are a few guidelines from NIST:
Secure Authentication
Use digitally signed or verified authentication tokens for secure access to microservices APIs.
Tokens should be handle-based or use a Hash-based Message Authentication Code (HMAC) scheme.
Apply restrictions to each API key based on the application and accessible APIs.
For stateless tokens such as JWTs, keep expiry times short and securely store the secret keys.
If using OAuth or OpenID Connect, ensure secure deployment.
Secure Access control
Define and provision access policies for all APIs and resources to an access server.
Enforce coarse-grained policies at the initial API gateway and finer-grained authorizations closer to the microservices.
Allow microservices to cache policy data, with expiry suitable to the infrastructure.
Access server should support fine-grained policies conveyed to microservices through standardized tokens, either handle-based or assertion-bearing.
Carefully control the scope of internal authorization tokens for each request.
Use the API gateway to centralize enforcement of authentication and access control for all microservices.
Implement mitigating controls like mutual authentication to prevent bypassing the API gateway.
API Security Monitoring
Perform security monitoring at both gateway and service levels
Detect and respond to inappropriate behaviors, including token reuse attacks and injection attacks
Log input validation errors, extra parameter errors, and system crashes
Use software like Akto for API Discovery and misconfigurations.
Display security parameters such as input validation failures and unexpected parameters on dashboard
API Scanning
Implement regular and thorough API scanning to identify vulnerabilities.
Utilize automated tools such as Akto for scanning that can handle complex API structures.
Ensure to scan public and private APIs as both can present significant security risks.
Prioritize the scanning of APIs that handle sensitive data or critical operations.
Review and update the API scanning strategy regularly to accommodate changes in the API landscape and advancements in security threats.
Incorporate the results from API scanning into your overall security posture assessment and improvement plan.
Service Discovery
Provide service registry capabilities through dedicated servers or a service mesh architecture.
Ensure the network housing service registry services is configured with Quality of Service (QoS) parameters for resilience and availability.
Use secure communication protocols like HTTPS or TLS for communication between an application service and a service registry.
Implement validation checks in the service registry to allow only legitimate services to perform registration, refresh operations, and service discovery queries.
Avoid tight coupling between an application service and an infrastructure service like a service registry.
Avoid service self-registration/deregistration patterns. Instead, use a third-party registration pattern.
Allow registration/deregistration of an application service only after performing a health check on it.
For large microservices applications, deploy a distributed service registry ensuring data consistency among multiple instances.
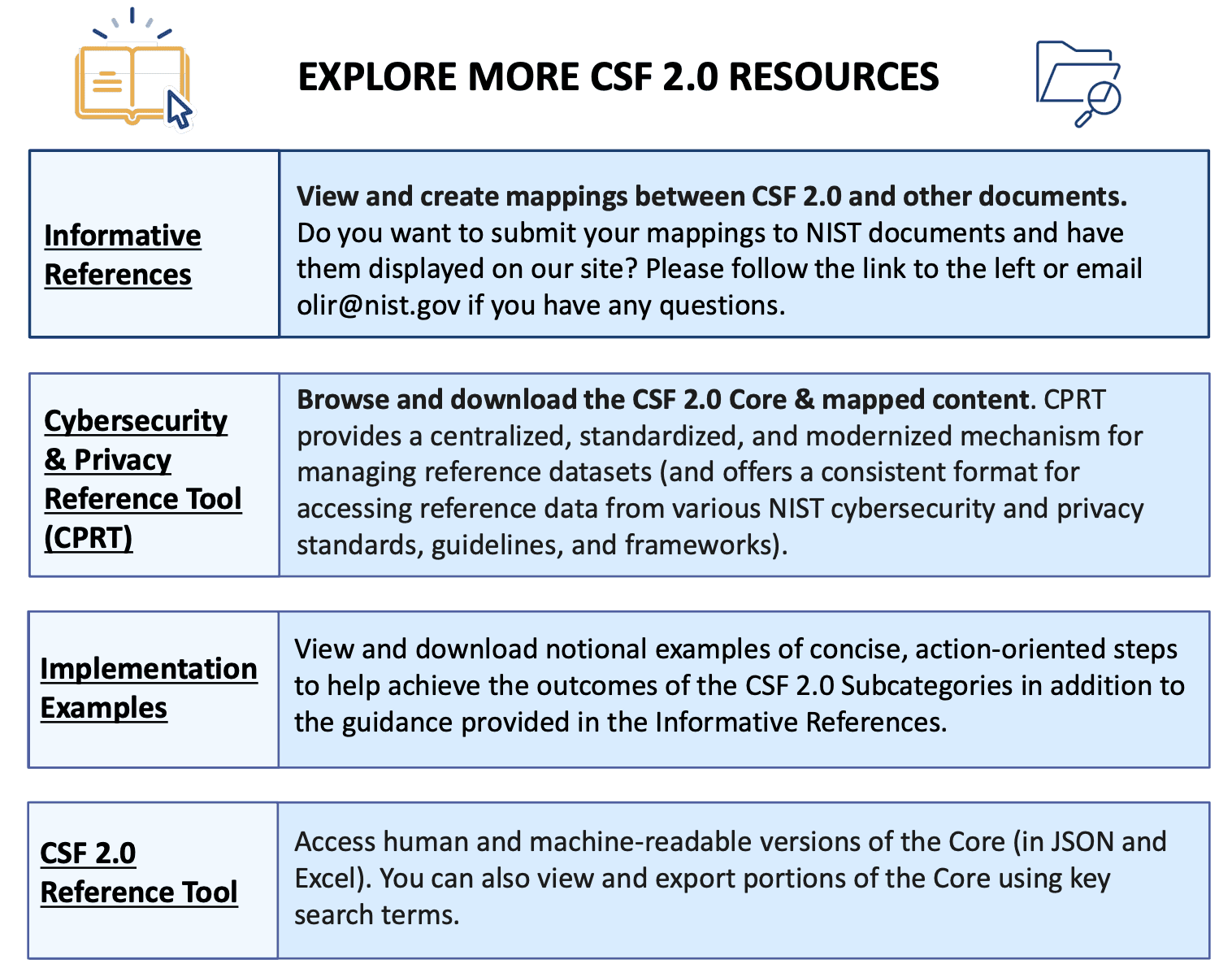
Tools and Resources on NIST 2.0 Framework
NIST offers an array of supplementary materials, such as:
Quick Start Guides - Best way to start in our opinion!
A dedicated CSF 2.0 Tool, to support organizations in implementing the Framework effectively.
Frequently Asked Questions on NIST Cybersecurity Framework 2.0
Q1: How did the development of CSF 2.0 happen?
Answer: The development of CSF 2.0 factored in comprehensive community feedback and continues to welcome stakeholder input.
Q2: Is compliance with CSF 2.0 mandatory?
Answer: No, compliance with CSF 2.0 is voluntary for the private sector. However, its extensive acceptance and integration into federal contracting requirements underscore its stature as a standard for cybersecurity practices.
Q3: What initiatives does NIST provide for adopting CSF 2.0?
Answer: NIST is dedicated to facilitating the understanding and adoption of CSF 2.0 through educational resources, workshops, and outreach programs. These cater to a diverse audience from small businesses to large enterprises and government agencies.
Q4: How often is the CSF updated?
Answer: The CSF is updated periodically to stay relevant with the evolving cybersecurity landscape. The latest version, CSF 2.0, was released in 2021.
Q5: Can small businesses benefit from implementing CSF 2.0?
Answer: Absolutely, CSF 2.0 is designed to be adaptable to organizations of all sizes and sectors. Small businesses can certainly benefit from the guidance provided by the framework to manage their cybersecurity risks.
Q6: How does the CSF 2.0 interface with other cybersecurity standards?
Answer: The CSF 2.0 is designed to complement, not replace, an organization's existing cybersecurity and risk management processes and cybersecurity standards. It can be used to support the implementation of various cybersecurity standards.
Q7: How can an organization measure its progress with the implementation of CSF 2.0?
Answer: Organizations can use the Profiles and Tiers in the CSF 2.0 to measure their progress. Profiles can help organizations align their cybersecurity activities with their business requirements, risk tolerance, and resources. Tiers can help organizations assess their current level of cybersecurity sophistication and identify areas for improvement.
Experience enterprise-grade Agentic Security solution
