9 Best AI Security Vendors and Companies in 2026
Discover the top AI security vendors and companies in 2026. Compare solutions for agentic AI, LLM protection and enterprise AI governance.

Kruti
Sep 16, 2025
Cybercriminals are becoming more advanced, leveraging machine learning and automation to bypass enterprise security defenses. In response, AI security providers are deploying artificial intelligence to improve threat detection, analysis, and incident response. Recent research shows that 74% of IT security professionals in the U.S. have experienced significant impacts from AI-driven cyberattacks. This raises a critical question for organizations: how can businesses protect themselves against these rapidly evolving cyber threats?
This blog helps enterprises understand AI security vendors, why they are critical, how to evaluate the right fit, and the major vendor categories in the market.
What are AI Security Vendors?
AI Security Vendors are technology providers that deliver AI-driven security solutions to protect enterprise systems, networks, and applications from modern cyber threats. An advanced AI Security Company uses machine learning, behavioral analysis, and automation to detect anomalies, prevent intrusions, and predict attacks in real time. Unlike traditional rule-based tools, AI security platforms from leading AI Security Vendors analyze large volumes of data to uncover hidden or emerging threats that manual methods often miss.
Through advanced threat detection, automated response, and predictive defense, the best AI security vendors help organizations improve visibility, reduce risk, and strengthen their overall security posture. By combining real-time intelligence with scalable automation, an experienced AI Security Company enables enterprises to defend against evolving cyber threats and build trust in a rapidly changing digital landscape.
How AI Security Vendors Protect Modern Organizations
Cyber threats are now smarter, quicker, and harder to stop with old security tools. Attacks are growing in number, and manual defenses often cannot keep up. AI security providers give the speed and intelligence needed to handle new risks.
Rising Sophistication of Cyberattacks
Attackers now use automation, AI and advanced tricks to slip past old security systems. Traditional tools often fail to detect new zero-day attacks or hidden intrusions. Best AI security vendors solve this with behavior analysis and anomaly detection. They uncover hidden threats that rule-based systems usually miss.
Overwhelming Volume of Threat Data
Security teams deal with millions of daily alerts, logs, and signals across hybrid environments. Manual review often causes alert overload and missed risks. LLM security vendors remove the extra noise, pick out the most important alerts, and handle triage automatically. This lets engineers spend time on the tasks that matter most.
Shortage of Skilled Security Engineers
The global cybersecurity talent gap leaves many organizations without adequate defense capabilities. According to ISC², the workforce gap reached over 4 million professionals in 2024. AI cybersecurity solutions reduce reliance on human-only analysis. Automation fills resource gaps while improving accuracy and speed.
Speed of Threat Evolution
Malware, ransomware, and phishing attacks change faster than signature-based defenses can keep up. New versions appear every day, leaving organizations at risk. AI-driven security keeps learning and adjusting to new attack methods. This allows faster detection and stronger defense against changing threats.
Compliance and Regulatory Pressure
Data protection laws demand continuous monitoring, reporting, and risk assessments. Manual compliance processes are resource-intensive and prone to error. AI cybersecurity vendors simplify compliance with automated auditing and reporting. This reduces regulatory risk while maintaining a strong security posture.

Join Aktonomy’26: The industry’s biggest Agentic AI Security Summit. Hear directly from CISOs and AI security leaders on how enterprises secure AI agents and MCP workflows in production. Feb 24 · Save your seat now!
AI Security Vendor Assessment Criteria
When thinking about how to evaluate AI security vendors, organizations should look at capabilities, accuracy, and flexibility. These AI security vendor selection criteria help ensure the chosen solution fits long-term security needs.
Technology and Capabilities
A good AI security provider offers tools to spot unusual activity, study behavior, and respond automatically. The solution should work in both local systems and cloud setups. This ensures protection that expands as the organization grows.
Accuracy and False Positives
AI cybersecurity solutions must detect threats with high accuracy while keeping false positives as low as possible. An excessive number of false alerts consumes time and resources, leading to slower response efforts. Vendors should have clear proof of accuracy supported by real-world results.
Integration and Compatibility
AI cybersecurity companies should seamlessly integrate with SIEM, SOAR, and endpoint protection tools. This minimizes the complexity of managing separate systems while automating security workflows. Easy integration with existing tools also enables faster threat detection, improved response times, and more efficient security operations.
Regulatory and Compliance Support
Leading vendors embed compliance reporting and automated auditing into their platforms. This reduces manual work while supporting regulations like GDPR, HIPAA, and PCI-DSS. Automated compliance also improves governance and lowers regulatory risk.
Vendor Reputation and Support
Strong customer support and a proven track record are vital when selecting the best AI security company. Look for references, case studies, and independent reviews. Reliable support ensures long-term value, seamless implementation and smoother adoption.
Types of AI Security Vendors
AI security vendors focus on different areas, giving solutions for endpoints, networks, APIs and full security platforms.
1. Endpoint Security Vendors
These vendors protect devices such as laptops, servers, and mobile devices from malware, ransomware, and other attacks. They use AI to find unusual activity and block threats before they can spread.
CrowdStrike Falcon

CrowdStrike Falcon delivers AI-driven endpoint detection and response with real-time visibility into attacks. Its cloud-based platform checks billions of events every day to detect threats accurately. Automated threat hunting and fixes reduce the time threats stay in the system. Its scalable design makes it a popular choice for large organizations.
SentinelOne

SentinelOne provides automatic endpoint protection using AI to spot new, unknown threats. Its platform combines detection, response, and recovery in a single solution. The rollback feature allows quick restoration after ransomware attacks. Strong automation reduces the need for manual work.
2. Network Detection and Response Vendors
These providers monitor network traffic to detect anomalies, intrusions, and stealthy attacks. AI allows to identify of hidden lateral movements and insider threats.
Darktrace

Darktrace uses self-learning AI to monitor network behavior and flag suspicious actions. Its Enterprise Immune System finds threats across cloud services, smart devices (IoT), and industrial systems. Automatic response stops attacks within seconds of detection. Visualization tools make investigation and incident response easier.
Vectra AI

Vectra AI specializes in AI-driven network detection and response with deep visibility into attacker behavior. It uses machine learning to uncover hidden command-and-control activity. Real-time detection significantly reduces attack dwell time. Integrations with SIEMs simplify workflows for security teams.
3. Protecting MCP, AI Agents, LLMs and APIs
Akto.io is an agentic AI security platform built to secure autonomous systems in production. It provides a unified trust layer for AI agents, MCP servers, GenAI applications, and the actions they take at runtime. Akto automatically discovers agents, MCP endpoints, tools, and agent-to-system interactions across cloud and endpoints, giving security teams visibility into what agents exist, how they connect, and what they can do. With 50+ connectors, Akto can be connected to virtually any environment to effortlessly capture AI agent, MCP, and API data across the entire stack.
Akto.io
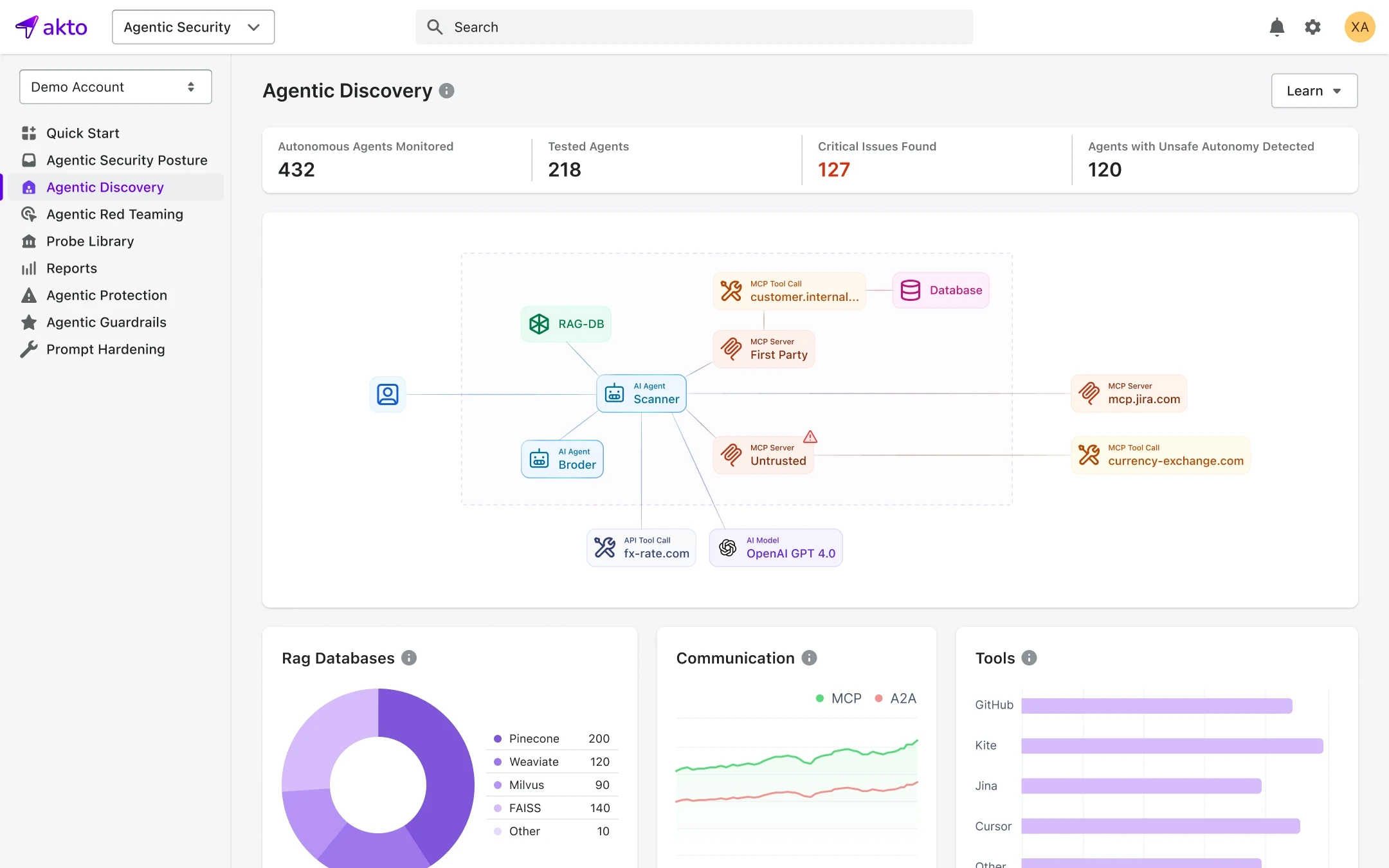
Akto enforces runtime control and guardrails for LLM-driven agents and MCP-based tool execution. It detects and helps prevent threats such as prompt injection leading to tool misuse, over-privileged agent actions, unsafe MCP calls, and unauthorized data access. Akto’s inline enforcement and continuous monitoring allow teams to define what agents are allowed to do-and stop risky actions before execution. Designed to integrate seamlessly into modern AI stacks, Akto enables organizations to secure agentic AI systems without slowing agent development or deployment velocity.
Salt Security

Salt Security allows AI-based API protection to detect unusual activity and prevent attacks. The platform monitors API traffic to uncover hidden vulnerabilities. Continuous learning enhances defense against emerging API threats, and detailed reports support compliance and management requirements.
4. SIEM/XDR Platforms with AI
These vendors include AI in larger platforms for security information, event management, and extended detection and response.
IBM QRadar

IBM QRadar leverages AI and advanced analysis to connect large volumes of log and event data. It identifies hidden threats and ranks them for quick investigation. Automated workflows improve incident response and reduce analyst workload. Cloud scalability supports security operations for large organizations.
Microsoft Defender

Microsoft Defender incorporates AI into its XDR platform for end-to-end protection. It integrates across endpoints, identities, email, and cloud workloads. Threat intelligence and automation reduce detection and response times. Native integration with the Microsoft ecosystem boosts efficiency for enterprises.
Palo Alto Cortex XDR

Cortex XDR combines data from endpoints, networks, and the cloud with AI-powered analysis. It detects sophisticated attacks accurately and provides context-based insights. Built-in automation quickens investigation and containment. A single platform reduces tool overload and simplifies operations.
Pricing Models of AI Security Vendors
Understanding AI security vendor pricing is essential for budgeting and evaluating solutions. Most vendors provide flexible pricing structures that allow you to pay for what you use, capabilities, or system size, depending on the vendor, and you can scale accordingly.
Subscription Pricing
Many AI cybersecurity vendors utilize a subscription model. They charge on a monthly or annual plan. The price depends on the number of endpoints, users, or assets being protected. This cost setup is for organizations that need long-term stability.
Usage-Based Pricing
Some vendors offer a pay-as-you-go model, where charges depend on data volume, traffic analyzed, or the number of API calls monitored. This pricing model suits organizations with fluctuating demand or seasonal activity.
Tiered Feature Packages
Vendors provide multiple levels, such as basic, advanced, and enterprise, with progressively more features and AI capabilities at each level.
Enterprise Licensing Agreements
Large enterprises may negotiate custom contracts that include services, integrations, and premium support. These agreements deliver cost savings at scale and provide flexibility for deploying AI security solutions across global systems.
Freemium and Trial Models
Some AI security vendors provide free trials or limited-feature plans, giving organizations the ability to evaluate effectiveness before committing. This reduces risk and allows faster, more informed decision-making for security teams.
Final Thoughts on AI Security Vendors
As AI adoption accelerates across enterprises, AI security has become a foundational requirement rather than a specialized add-on. At the same time, AI-driven threats and attack techniques are becoming more sophisticated, exploiting weaknesses in AI workflows, integrations, and runtime behavior that traditional security tools were not designed to address. Risks now extend beyond model misuse to include unauthorized actions, data exposure, and abuse of AI-enabled interfaces at scale.
Effective AI security platforms must therefore provide continuous visibility, policy enforcement, and runtime monitoring across AI components, including LLMs, AI-powered applications, and the systems they interact with. Akto addresses these requirements through unified discovery, real-time monitoring, and enforcement across AI and API environments. Its support for runtime guardrails, automated risk detection, and broad integration coverage enables security teams to identify and mitigate emerging AI threats consistently across cloud and hybrid environments.
Important Links
Experience enterprise-grade Agentic Security solution
