
Introducing Akto + Cursor: MCP Security Inside the IDE
Learn how Akto’s integration with Cursor enables MCP Guardrails, helping teams secure, monitor, and govern AI agent access across enterprise systems.

Akash
Dec 31, 2025
As agentic AI adoption accelerates, MCP servers are becoming a core part of how developers connect tools, data sources, and autonomous agents, often directly from their development environment. Increasingly, these interactions don’t happen in production first. They happen in the IDE.
Cursor sits at the center of this shift.
But while MCP adoption inside developer workflows has moved fast, security controls haven’t kept pace. Most teams still lack runtime visibility into MCP requests and responses, meaningful guardrails to prevent unsafe tool execution, and reliable detection of sensitive data exposure caused by agent actions.
Today, we’re introducing MCP Guardrail integrated with using Cursor Hooks, to bring runtime security directly into agentic workflows at the IDE layer.
Introducing Akto MCP Guardrail for Cursor
Akto’s MCP Endpoint Shield for Cursor provides runtime MCP security using Cursor’s native hook system.
Cursor Hooks allow scripts to run at specific points in the agent lifecycle, including before an MCP execution and after its completion. This makes it possible to integrate real-time security controls directly into developer workflows without modifying MCP servers or agent logic.
These hooks give Akto two critical control points:
Before an MCP invocation is sent to the MCP server, where Akto can inspect the request, evaluate policies, and prevent unsafe operations from executing.
After an MCP response is received, where Akto can analyze outputs for sensitive data, unsafe content, or signs of misuse, and take action such as redaction or blocking.
This approach requires no changes to MCP servers, no additional developer tooling, and no disruption to existing workflows. Security controls operate transparently, while developers continue working as usual. Learn more
How Akto MCP Guardrail Works with Cursor Hooks
Cursor Hooks give Akto the ability to insert security controls before and after MCP execution within the agent loop.
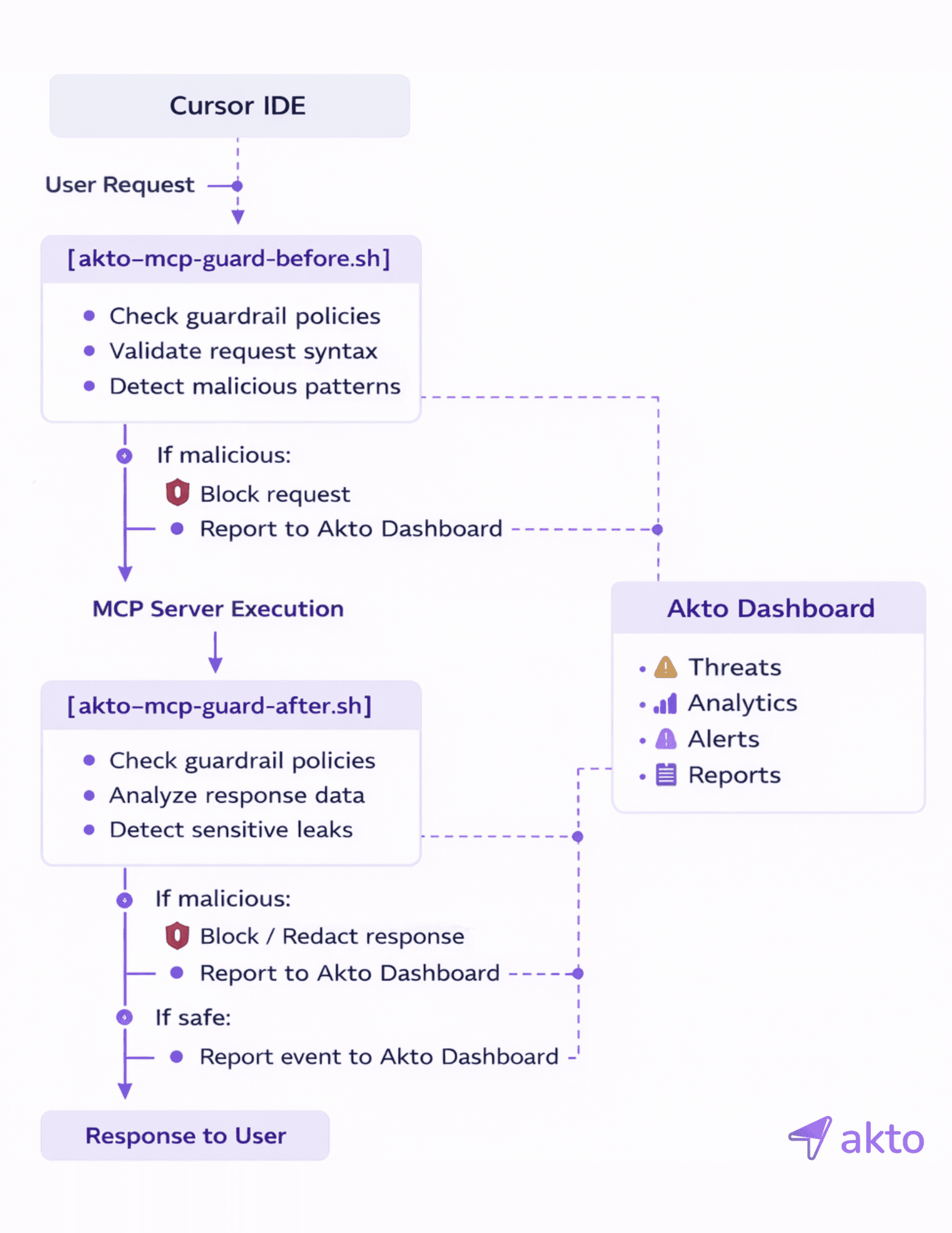
Before MCP execution: Request inspection
The moment the agent generates an MCP request, Cursor triggers the beforeMCPExecution hook.
At this stage, the MCP request has not yet reached the MCP server. It exists entirely inside the IDE. Akto’s guardrail script (akto-mcp-guard-before.sh) runs here and inspects the request in real time.
Akto evaluates the request against guardrail policies:
Whether the request structure is valid
Whether the prompt or parameters contain malicious patterns, such as prompt injection attempts or unsafe commands
If Akto determines that the request is malicious or violates policy. For example, an injected instruction to read environment variables or access restricted data. the request is blocked immediately. The MCP server is never called.
After MCP execution: Response inspection
When the MCP server returns a response, Cursor triggers the afterMCPExecution hook.
Akto’s post-execution guardrail script (akto-mcp-guard-after.sh) now inspects the response payload before it reaches the agent or the user. This step is critical because even legitimate requests can result in risky responses.
At this stage, Akto analyzes the response for:
Sensitive data exposure, such as credentials, tokens, or PII
Unsafe or restricted content
Policy violations related to data handling
If sensitive data is detected, Akto can redact or block the response before it is consumed by the agent. As with request blocking, the event is reported to the Akto dashboard with full context.
If the response is safe, it is passed through unchanged and delivered to the user.
Visibility and Audit

Throughout this entire flow, whether requests or responses are blocked, redacted, or allowed. Akto reports all events to the central dashboard.
Security teams gain real-time visibility into:
Which MCP servers are being used inside Cursor
What tools agents are invoking
Which actions were blocked or allowed
Where sensitive data exposure was detected
This visibility exists without slowing down developers or requiring them to change how they work.
Developer velocity, governed at runtime
Every major AI tool is adding agentic capabilities: Cursor. Claude. VS Code. GitHub Copilot.
Developers will use them with or without a centralized security strategy. Agentic AI adoption moves bottom-up, through developer workflows, long before governance frameworks or security reviews catch up.
Akto’s MCP Guardrail for Cursor gives security teams a way to get ahead of that curve-by enforcing guardrails exactly where agentic actions occur.
No disruption to developer velocity.
Ready to see Akto in action? Schedule a demo here
Experience enterprise-grade Agentic Security solution
