MCP Proxy: Secure & Scalable AI Agent Workflows
Learn key MCP Proxy benefits, security features, and best practices for safe, scalable AI agent and MCP workflow management in enterprises.

Bhagyashree
Dec 4, 2025
As organizations grow their AI implementations, many are beginning to realize that direct, point-to-point connections between AI applications and backend systems are not always scalable, secure, or maintainable. To address this, a Model Context Protocol Proxy (MCP Proxy) is increasingly being adopted as a central routing layer for MCP traffic. It sits between MCP clients and MCP servers, forwarding requests and responses during MCP transactions.
While this architectural approach can improve visibility, governance, and control, it is important to understand that MCP itself is still a young and evolving protocol. Recent research has shown that MCP servers can introduce security risks if not properly vetted or configured, and that the broader MCP ecosystem contains many low-quality or abandoned projects. Because of this, simply inserting a proxy does not automatically eliminate risk-organizations must still enforce strong guardrails, validate MCP servers, and continuously monitor traffic passing through the proxy.
This blog explores what an MCP Proxy is, how it works, and what factors must be considered to implement it effectively in real-world, enterprise environments.
What is MCP Proxy?
An MCP Proxy is an intermediary layer between MCP clients (AI applications) and MCP servers (tools and data sources). It receives client requests, routes them to the correct MCP server, collects responses, and returns them to the client. From the client’s viewpoint, the proxy behaves like a unified MCP server; from the backend’s view, it behaves like a client. This centralization simplifies connectivity, standardizes communication, and gives organizations better operational control. However, MCP Proxy does not guarantee security or governance on its own-these must be implemented deliberately. Recent research shows the MCP ecosystem is still maturing, and untrusted MCP servers can introduce significant risks. Using remote or third-party MCP servers requires strict authentication, validation, and monitoring. A proxy becomes a high-value target, so it must be carefully secured and observed.
When properly designed, an MCP Proxy can streamline routing while enabling safer, more controlled MCP interactions.
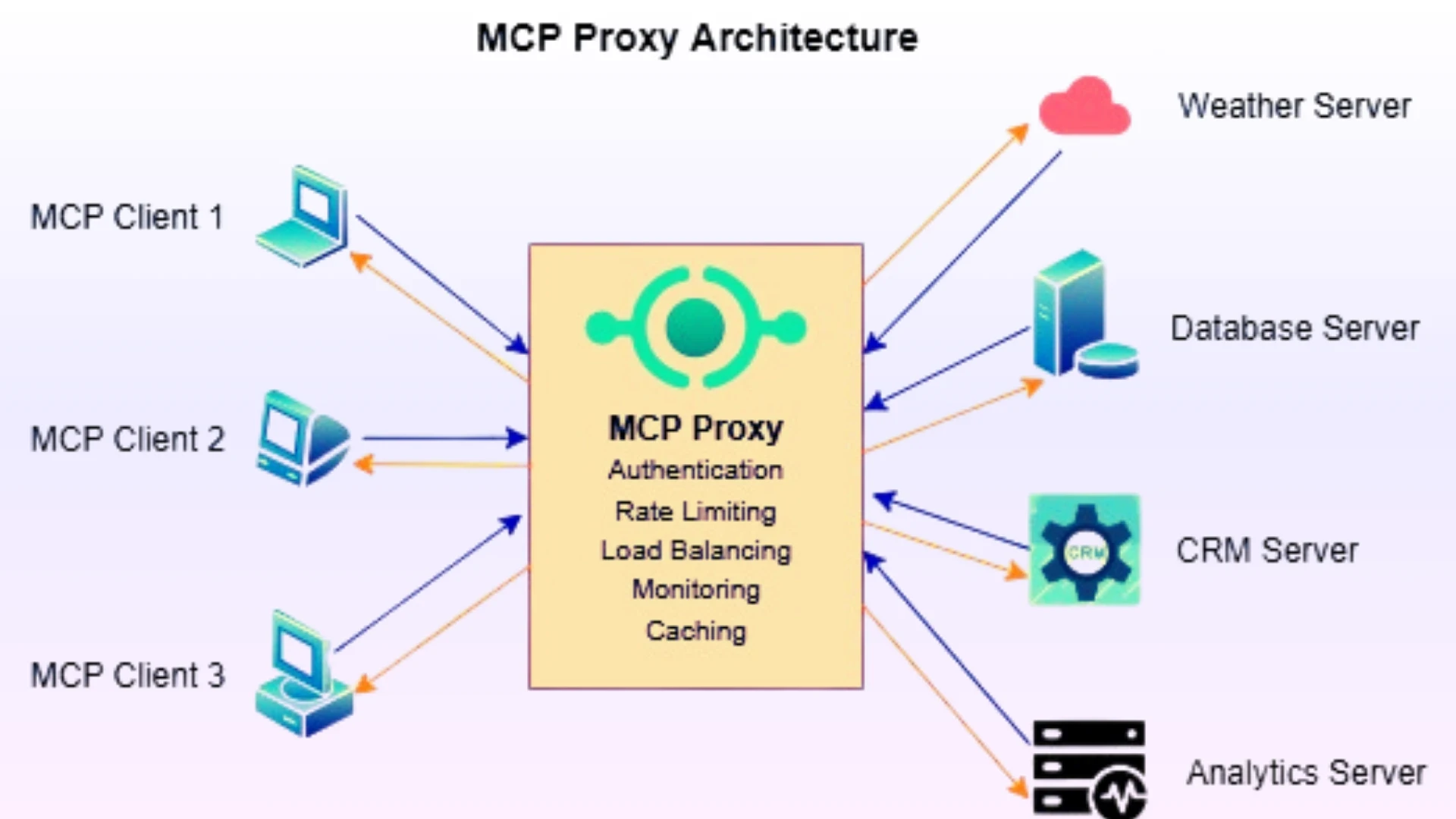
Why MCP Proxy is Important
MCP proxy is essential for organization for multiple reasons. Here’s why.
Access Control and Governance
MCP Proxy implements RBAC, user isolation and audit compliance by adding identity platforms to ensure only verified authorized teams are granted necessary access to MCP servers under centralized enterprise governance.
Manageability at Scale
MCP-Proxy systematically organizes sprawling MCP environments by keeping a server registry, adopting protocol versions, managing sessions, monitoring and facilitating both external and internal MCP servers efficiently.
Security and Authentication
An MCP proxy protects communication by adding OAuth 2.1, verifying requests for threats such as data leaks, prompt injection and routing all MCP traffic via a controlled, trusted endpoint.
Telemetry and Observability
MCP Proxy offers complete visibility with request tracking, error logs, performance metrics and audit trails which enables proactive monitoring, secures oversight and troubleshooting of MCP usage.
Features of MCP Proxy
Here’s a breakdown of MCP proxy features:
MCP Registry and Server Management
Offers a unified catalog for private and public MCP servers, to store complete metadata, authentication rules, capabilities and access policies to ensure consistent, governed enterprises operations.
Manages OAuth2 flows safely stores, refreshes tokens and implements user-level authorizations by removing decentralized credential issues and providing IT comprehensive visibility and compliance control.
Lets autonomous agents to discover and invoke tools, one at a time without hardcoded configurations, that support adaptive AI systems that keep evolving with organizational changes and new internal capabilities.
MCP Access Control and MCP Authentication
Centralizes OAuth2, individual access tokens and virtual account tokens to simplify enterprise identity management and eliminate the overhead of managing multiple server credentials.
Embeds fine-grained role based permissions, ensures users and applications access are only restricted to authorized MCP servers and allows stringent governance for critical workloads and regulated environments.
Automates token refresh and secure storage and maintains complete audit trails by significantly minimizing developer burden and harden security across all the distributed MCP environments.
MCP Invocation and Tool Orchestration
Automatically prefixes tool names with server identifier to avoid naming collisions, enables unified discovery and maintain consistent access when multiple servers display similar tool functions.
Gathers all servers platforms into a single list_tools response to eliminate the need for multiple client-side connections and simplifies how agents navigate enterprise tool ecosystems.
Co-ordinates tool invocations across several servers, helps AI agents to build comprehensive automation workflows that effortlessly blends with enterprise data and systems.
How does MCP Proxy work
Here’s a series of steps on how MCP Proxy Works.
Accept Client Request: MCP Proxy accepts the clients JSON-RPC request through the SSE, HTTP streaming or WebSocket to set up session context and capture client metadata.
Validate and Authorize: Implement OAuth 2.1 / identity provider flows, validate tokens, deploy security policies and confirm RBAC permissions before going ahead with the request.
Routing: Utilizes the server registry, routing routes and metadata to choose the proper backend servers that meet policy requirements.
Protocol Mapping: Format and adapt the request to backends transport/protocol (JSON-RPC mapping, headers, WebSocket frames, preserve conversation context and metadata.
Verify and Enforce: Runs policy checks (prompt injection, DLP, content filters through built-in logic or third-party webhooks. Block, redact or sanitize payloads when required.
Forward and aggregate: Sends translated requests to backend, collect responses, combine or reconcile multi-server results and send output to clients.
Maintain Continuity: Stores conversation context and session IDs. Allows connection pooling and reuse connections to lower latency for continuity.
Fault Tolerance: Spreads the traffic across instances, adds circuit breakers for failing servers and reroute the requests to maintain consistent availability.
Log and Telemetry: Identifies performance bottlenecks, track performance metrics and error logs and conduct audits trails. Secures sensitive content through controls to track who accesses the logs.
Respond to Client: Returns to unified JSON-RPC response to client, updates session state and metrics for monitoring the governance systems.
Factors to Consider when implementing MCP Proxy
Here are some factors to consider when implementing MCP Proxy:
Technical Implement Challenges
Implementing an MCP Proxy needs a effective managing stateful sessions, management of protocol variations across servers and create intelligent error-handling systems. Make sure to achieve consistent behavior, proper version negotiation and smart circuit breaking enables major architectural complexity.
Resource and Performance Management
Optimize connection pools, caching strategies and batching logic that requires thorough understanding of tool behavior and usage patterns. Misconfigurations can lead to bottlenecks, due to resource exhaustion or increase in latency. Hence, making careful performance tuning is essential.
Security and Compliance Considerations
Managing authentication tokens, implementing strong data privacy controls and fine tuning rate limits are essential factors. The proxy should safely manage sensitive data and should safeguard backend servers without compromising user experience or violating compliance requirements.
Operational and Organizational Challenges
Running an MCP Proxy needs sophisticated monitoring, co-ordinated deployments and reliable backup approaches. Teams should maintain observability, sync updates with backend servers and ensure major recovery to avoid outages and enable business continuity.
MCP Proxy Implementation Process
Implementing an MCP Proxy involves planning, setup, and deployment to securely manage traffic between AI clients and backend servers. It ensures centralized control, enforces security policies, and enables observability across your MCP ecosystem for safe and scalable AI operations.
Planning and Design
MCP Proxy deployment begins with proper planning on server discovery, scalable deployment topologies, and integration with enterprise systems such as identity providers, load balancers, API gateways and monitoring platforms to enable seamless, future proof operations.
Implementation Setup
A baseline MCP proxy setup comprises of proxy server management, client communication, backend managers translating MCP interactions and authentication modules that implement identity policies to ensure secure, consistent and effective between clients and MCP servers.
Enterprise Implementation with Akto
Akto MCP proxy offers a centralized governance and security layer which allows threat protection, policy enforcement and guardrails for all MCP traffic and maintain effortless, direct connectivity to backend MCP servers across enterprise environment.
Production Deployment Considerations
Production deployments need high availability through multiple proxy instances and load balancers, autoscaling depending on usage metrics and strict security measures including secret management, network policies, encryption and continuous audits to retain compliance and resilience.
Best Practices to Implement MCP Proxy Effectively
Here are some best practices to follow when implementing MCP Proxy.
Regular Policy Updates: Keep security policies and guardrails up-to-date
Monitor Alert Fatigue: Fine-tune detection rules to reduce false positives
Performance Optimization: Utilize caching for frequently accessed resources
Backup Configuration: Maintain fallback options for critical MCP servers
Regular Audits: Continuously review logs and analytics for security insights
Final Thoughts on MCP Proxy
The future AI evolution depends on building intelligent models and creating intelligent architectures that can flexibly adapt, scale, and protect these features for real-world deployment. MCP Proxy serves as a significant component of this smart architecture, facilitating organizations to achieve full potential of the Model Context Protocol while aligning the requirements of enterprise production environments.
Implement governance for Your MCP-Traffic at Scale with Akto MCP Proxy. Centralize all your MCP client-to-server interactions, gain full visibility, apply real-time protection and ensure every request from your AI agents is secure and compliant. Book a demo right away to explore more on Akto's Agentic AI and MCP security.
Related Links
Experience enterprise-grade Agentic Security solution
