Akto Now Secures Clawdbot(Openclaw) on your Employee Devices
Visibility, governance, and guardrails for Clawdbot(Openclaw) as employee adoption accelerates

Krishanu Borah
Jan 30, 2026
Clawdbot(Openclaw) has taken the internet by storm. Many are calling it the closest we've ever been to a true personal AI assistant.
And now, this viral AI agent has become the fastest-growing shadow AI risk in the enterprise.
ClawdBot(Openclaw) is already inside your organization
On January 24, 2026, Clawdbot(Openclaw) was a niche GitHub project. By January 29, it had 101K stars. Today, it's crossed 107K and is still climbing.
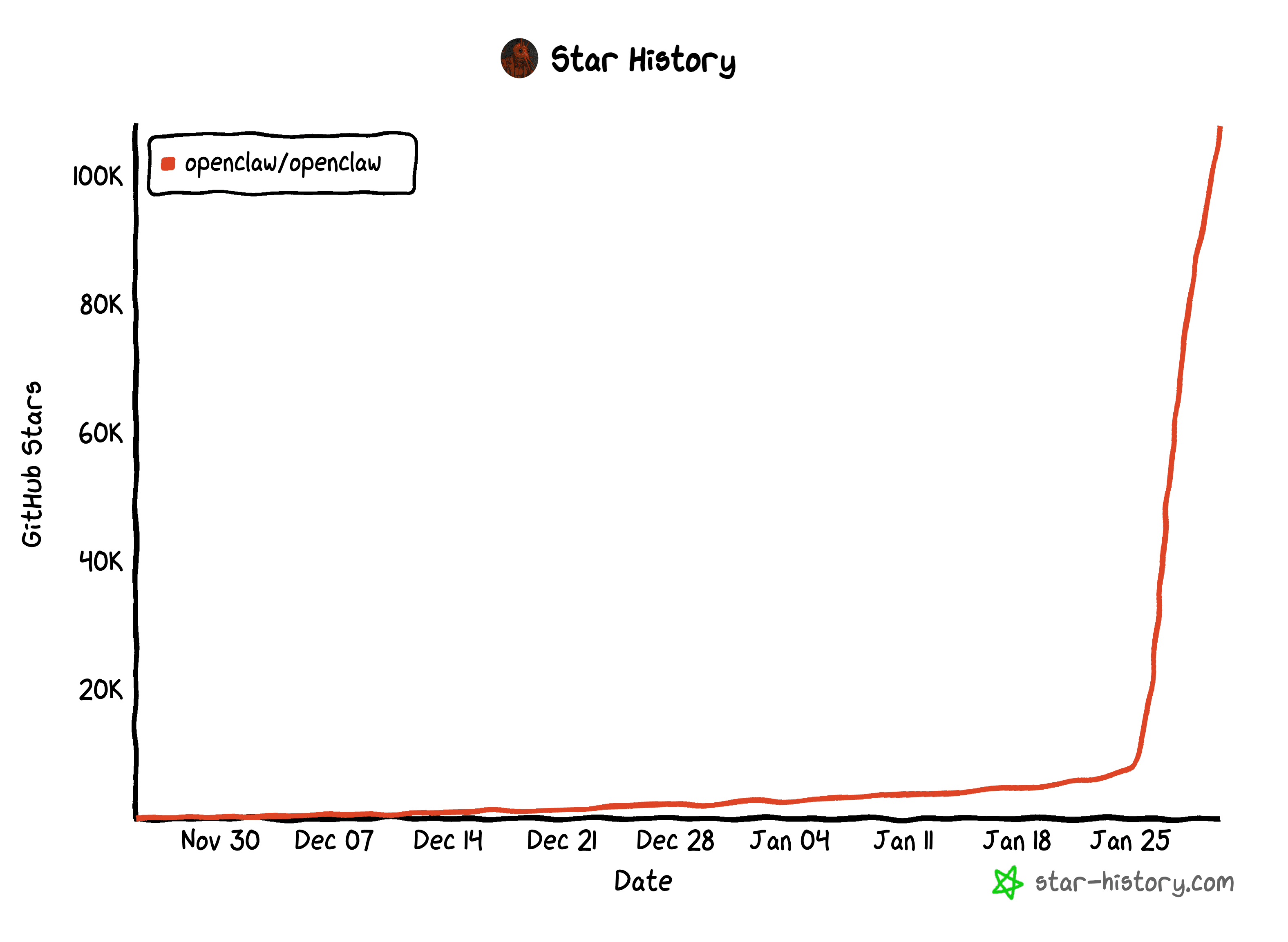
Employees didn't wait for IT approval. They didn't read the security docs. They saw the hype, ran the install script, and gave an AI agent root access to their machines.
Why ClawdBot(Openclaw) is different (and a massive risk for your enterprise)
Clawdbot(Openclaw) is an open-source personal AI assistant that runs locally on your system and integrates with messaging platforms like WhatsApp, Telegram, Slack, Discord, Microsoft Teams and iMessage.
It operates with delegated authority, able to access and perform the same actions as the user and keeps working even when you’re not working.
That's exactly what makes it dangerous.
Once enabled, it doesn't wait for permission. It can autonomously execute shell commands, fork repositories, make commits, send messages, and access files - all without asking.
By design, it introduces several critical risks:
Always reachable: Runs as a persistent background service, allowing actions to be triggered remotely via messaging platforms - no VPN or endpoint access required.
No identity boundaries: All users in a chat share the same level of access, with no per-user authorization or role separation and no identity aware policy enforcement.
Autonomous shell execution: Can indepedently execute arbitrary commands, modify files, fork repositories, and make commits A single prompt injection can result in destructive commands, credential exfiltration, or irreversible system changes.
Untrusted skill supply chain: The ClawdBot(Openclaw) skill marketplace introduces material supply-chain risk. Demonstrated vulnerabilities have enabled remote code execution within hours of skill deployment,
Implicit localhost trust: ClawdBot(Openclaw) trusts localhost connections. Behind a misconfigured reverse proxy, the entire internet looks like localhost to the bot.
Plaintext credentials: API keys, OAuth tokens, Signal pairing URIs-all stored unencrypted. One compromised endpoint exposes everything.
Common root execution: Many users run it as root, granting full control over the host system.
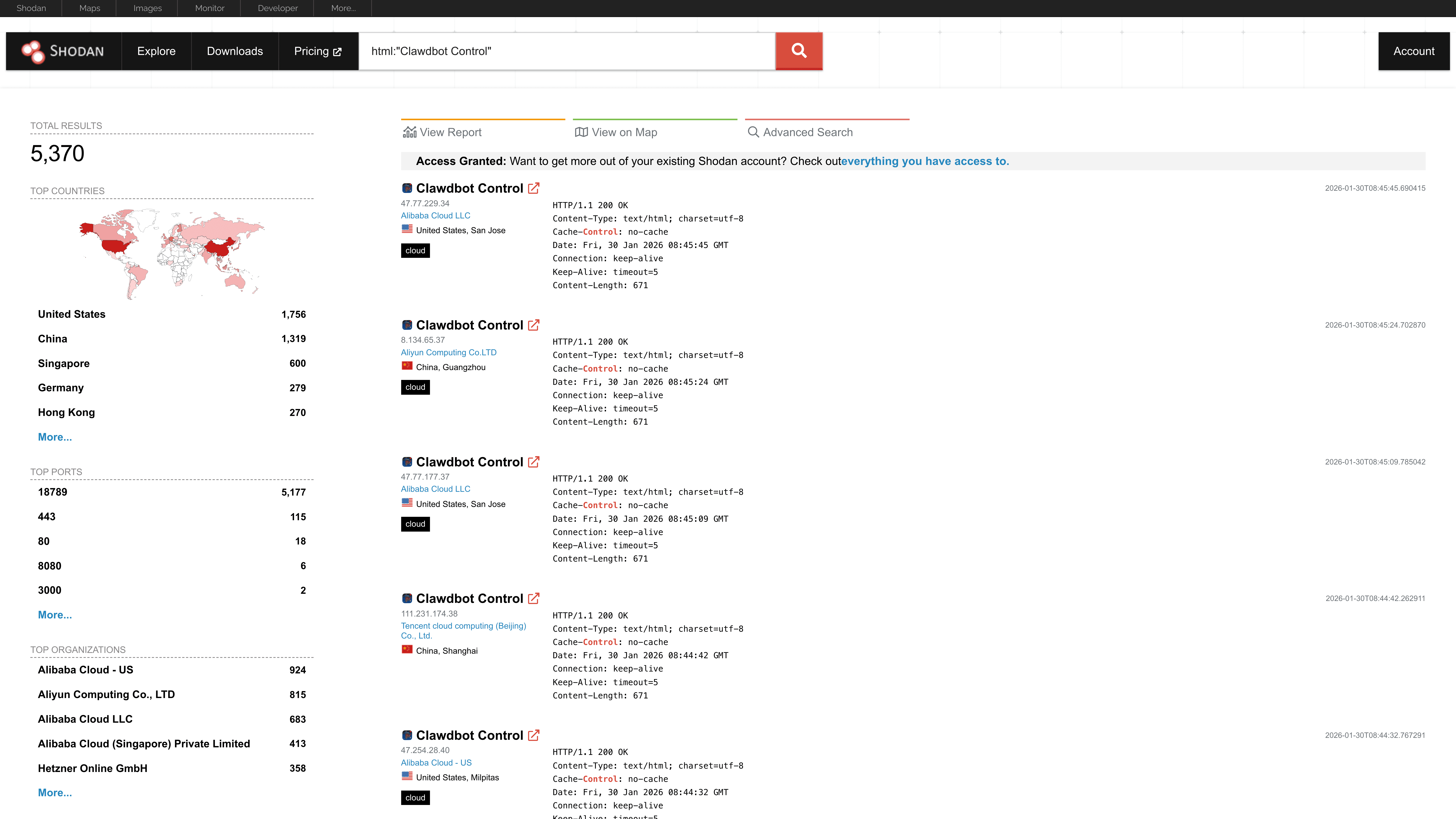
Public internet scans already show the scale of exposure. A single Shodan query for html:"Clawdbot Control" identifies 5,000+ exposed Clawdbot(Openclaw) gateways, many with no authentication controls, leaking
Claude, OpenAI, and Gemini API keys
VPN credentials, enabling ransomware access paths
Jira and Confluence tokens with corporate wiki access
Full conversation histories, including operational plans and sensitive data”
Akto now secures ClawdBot(Openclaw) with Discovery, Guardrails and Governance
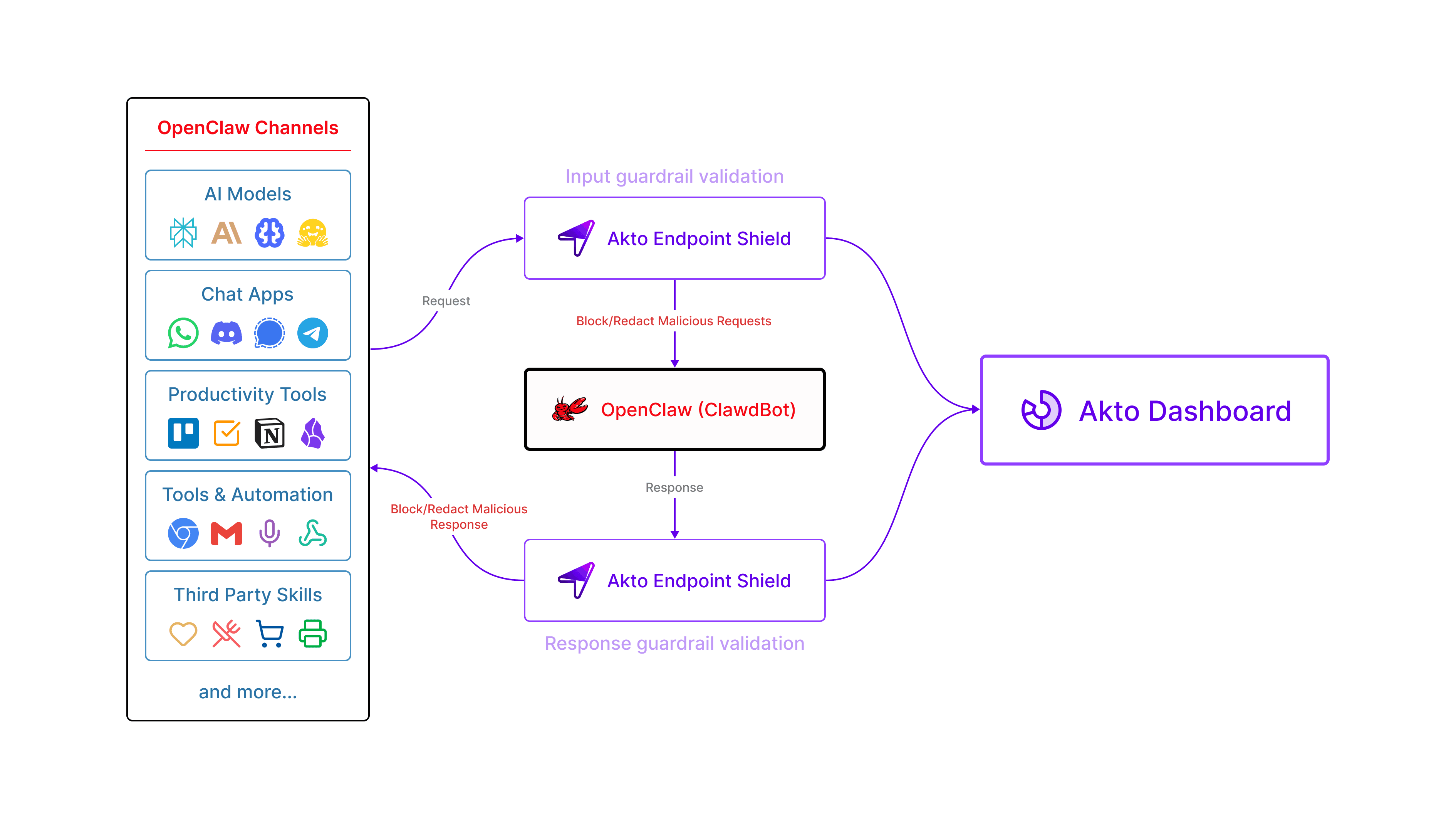
Akto provides native discovery and security controls for ClawdBot (OpenClaw) running on employee endpoints, allowing security teams to move from blind spots to enforceable governance.
1. Discover Where ClawdBot(Openclaw) Actually Runs
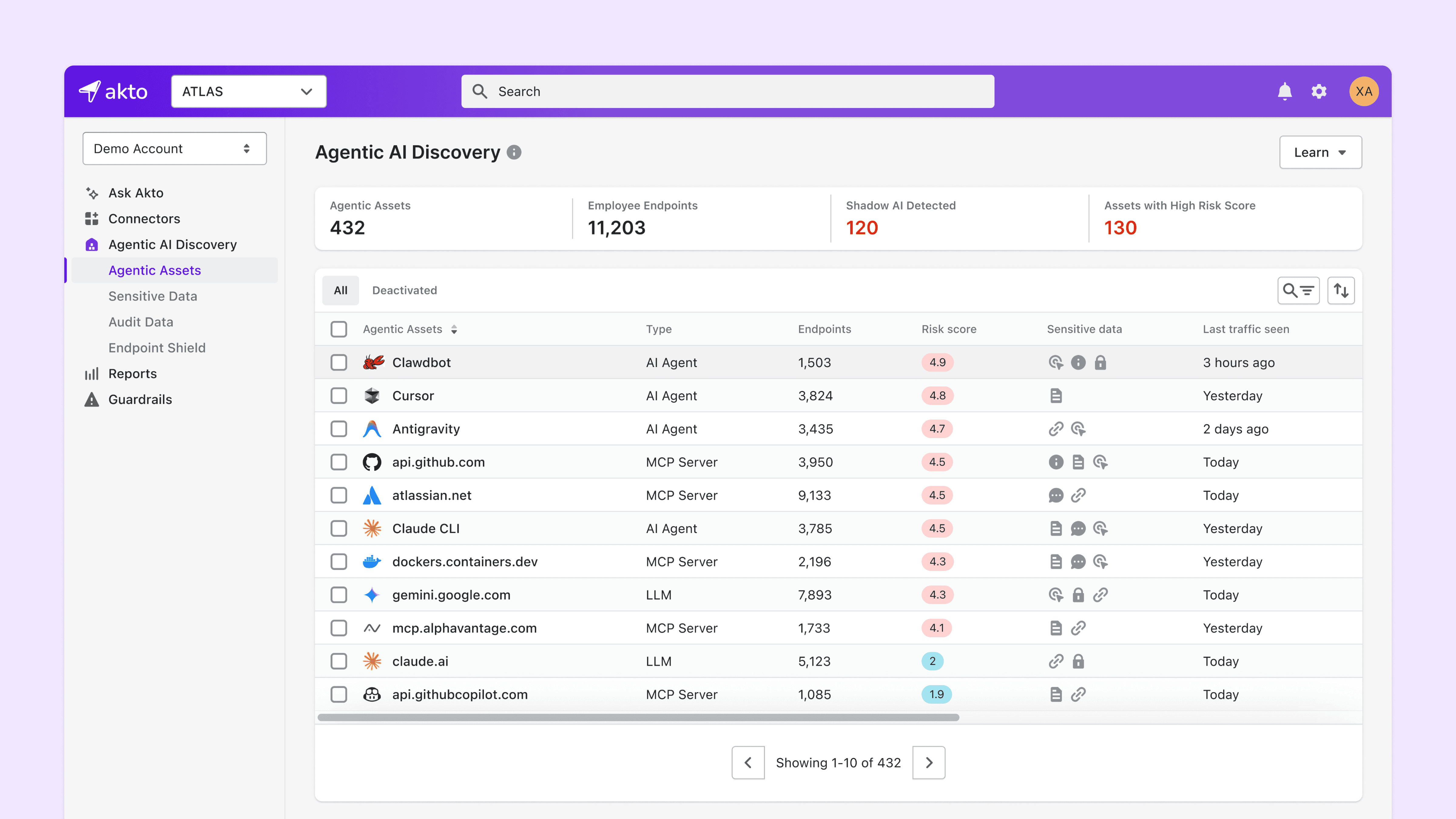
ClawdBot(Openclaw) doesn’t live in your cloud account or behind an AI gateway. It lives on employee endpoints - installed quietly, running persistently, and operating with delegated user authority.
Akto Atlas discovers ClawdBot(Openclaw), where it actually runs using the Akto Endpoint Shield Agent. Without relying on user disclosure or manual audits, Atlas identifies:
ClawdBot(Openclaw) installations across employee devices
Persistent background execution
Environments where the agent is active (developer machines, laptops, workstations)
2. Contextual Mapping of ClawdBot(Openclaw) Behavior
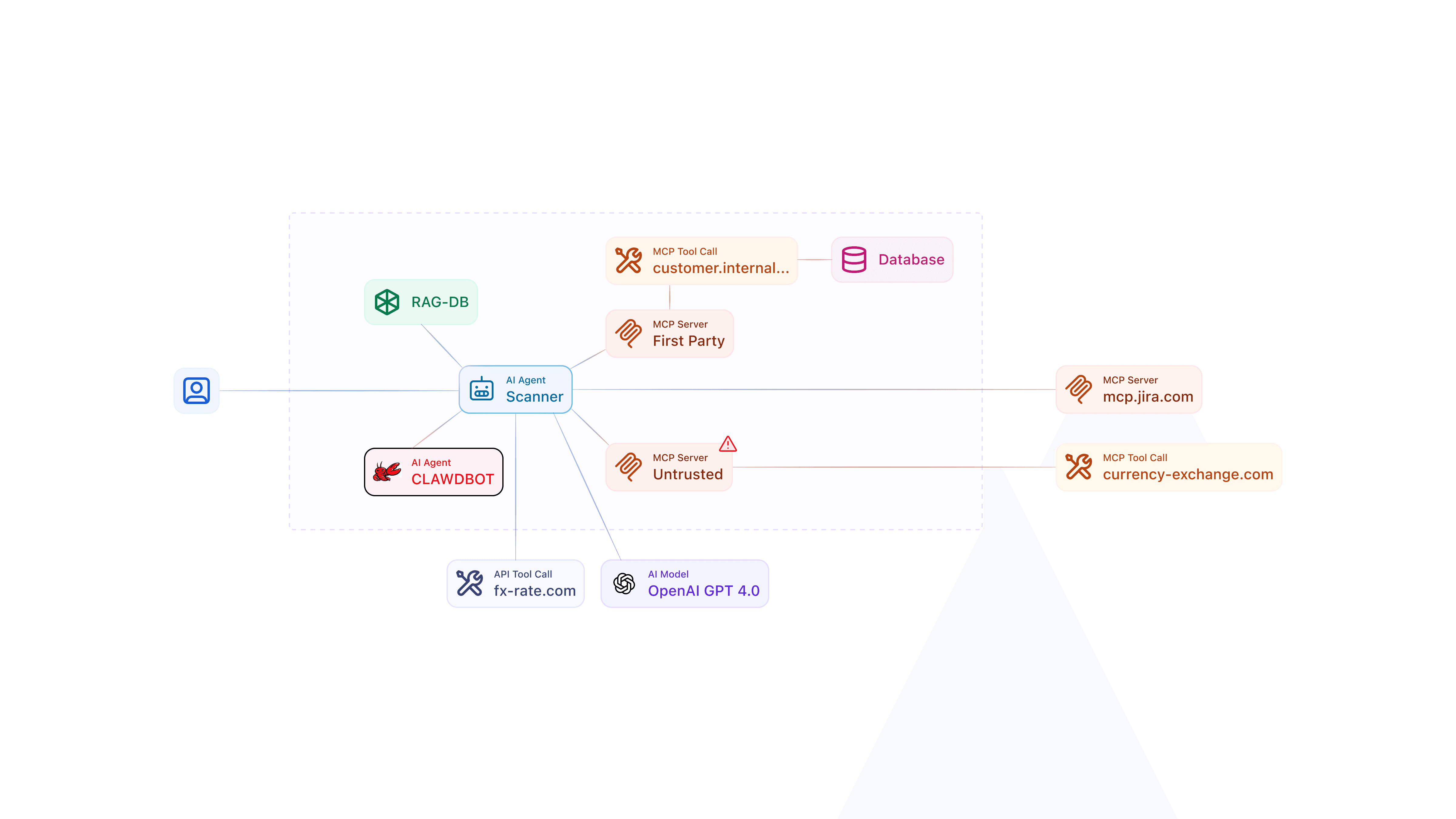
Finding ClawdBot(Openclaw) is only the first step. The real risk lies in what it does next.
Once discovered, Akto Atlas automatically maps ClawdBot’s activity, including:
Agent executions and command invocations
Interactions triggered via messaging platforms
Access to local files, repositories, and credentials
Data flows between the agent, tools, and external services
This allows security teams to quickly understand:
Where ClawdBot(Openclaw) has delegated authority
What actions it is capable of performing
Which endpoints represent the highest blast radius
Where sensitive data may be exposed or exfiltrated
Akto turns ClawdBot(Openclaw) from a black box into an observable, auditable agent.
3. Enforce Guardrails for the Destructive Agent by Akto
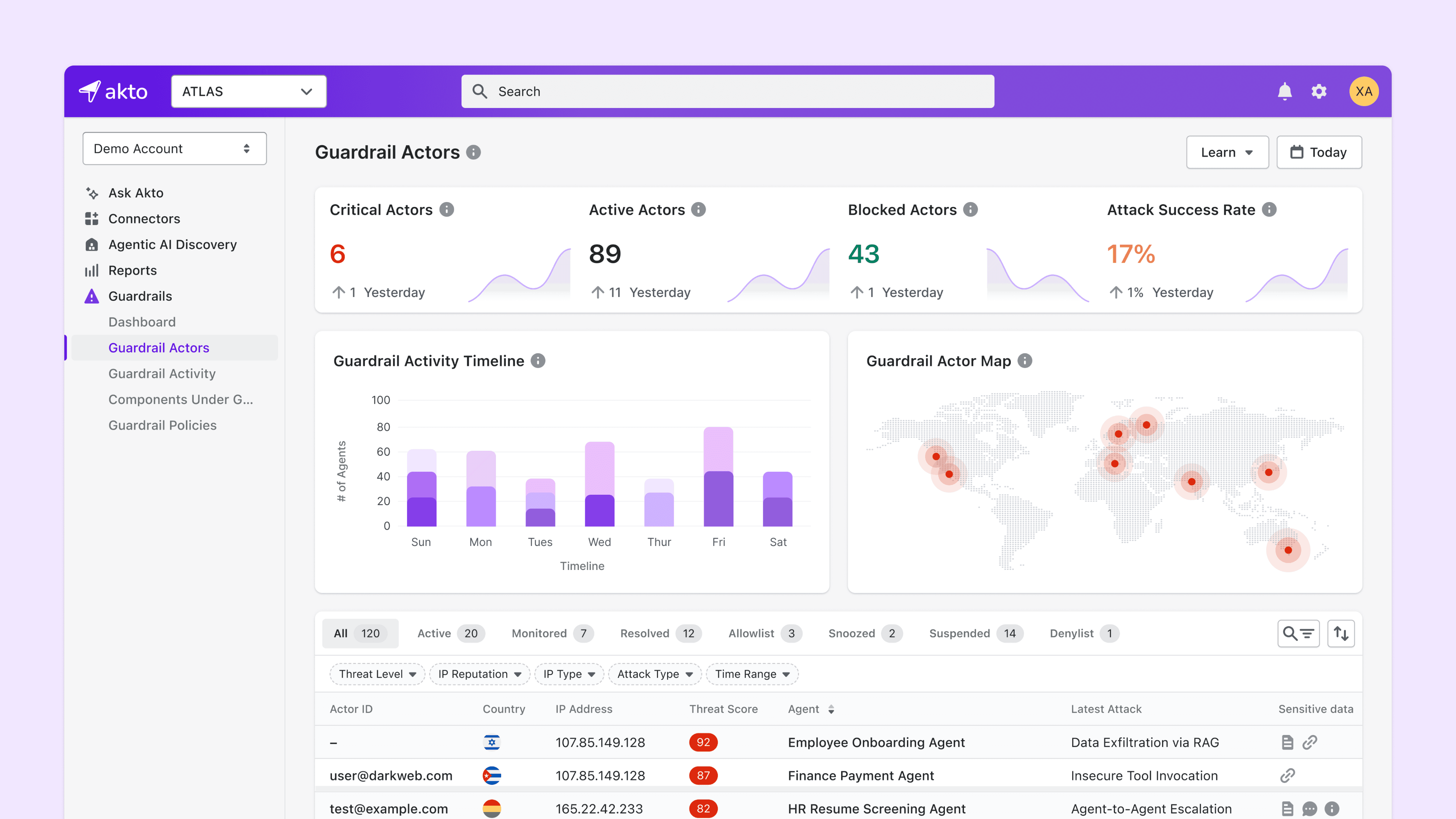
ClawdBot(Openclaw) was never designed with enterprise governance in mind. Akto fills that gap.
With Atlas, security teams can apply critical and high-severity AI guardrails to ClawdBot(Openclaw), enabling them to:
Detect and flag unapproved ClawdBot(Openclaw) usage
Enforce policies around agent execution and persistence
Reduce risk from overly privileged or misconfigured deployments
Bring ClawdBot(Openclaw) under centralized AI governance controls
Governance is no longer a policy document - it becomes continuous, enforceable control, even for agentic AI running on employee devices.
The AI Agent Risk Model Has Changed
ClawdBot(Openclaw) is just the beginning. Over the next year, autonomous agents will rapidly expand as personal assistants and workflow operators - each introducing new architectures and attack surfaces that legacy security controls were never designed to handle.
AI Governance Can’t Be Optional
Waiting for the next viral agent means accepting blind spots by default. If you don’t know what’s already running on your endpoints, your security posture is reactive by design.
Security should scale with innovation.
Schedule a call with Akto to gain visibility into your AI agents and MCP servers, identify emerging agentic AI risks, and enforce controls before they turn into incidents.
Experience enterprise-grade Agentic Security solution
